Hackers have found options for stealing cryptocurrency through the anonymous TOR browser. This conclusion was madean anonymous researcher with the pseudonym Nusenu during the analysis of the browser.
The program operates on the basis of the systemonion routing. Thanks to her, projects and netizens can remain anonymous while surfing the dark web. TOR operation is provided by the output nodes of the network. It was them, according to Nusenu, that the attackers attacked.
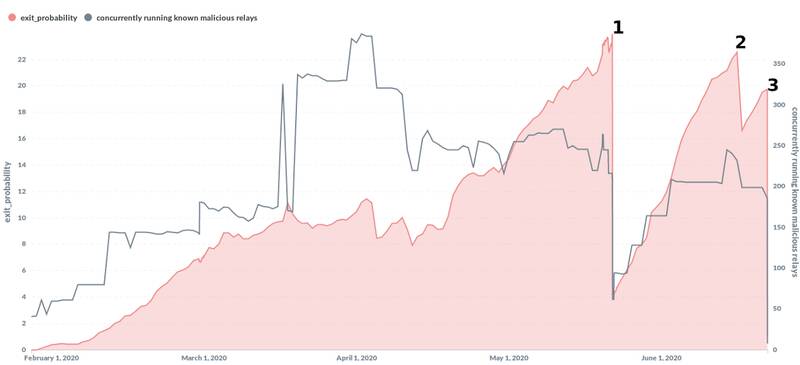
Hackers have been exploiting this loophole for a long time, Nusenu said. According to conservative estimates, in May 2020, hackers controlled about 25% of the nodes.
By capturing the data, the scammers were able to falsify user traffic data. They replaced traffic from HTTPS addresses to HTTP, artificially reducing the security of the information channel.
To obtain cryptocurrency through traffic interception, hackers "caught" the numbers of bitcoin wallets in the stream and replaced them with their own. In this way, the victims voluntarily funded the accounts of the hackers.
After discovering the vulnerability, Nusenu notified the browser developers about it. And despite the fact that all necessary measures have been taken so far, hackers still control about 10% of traffic.

Rate this publication