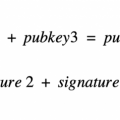Bitcoin users may soon be able to take advantage of the technology's benefits.called Taproot. First proposed by Bitcoin Core developer and former tech. by Blockstream Director Gregory Maxwell, Taproot aims to increase the flexibility of Bitcoin smart contracts while enhancing their privacy. This will make even the most complex smart contracts on the blockchain generally indistinguishable from regular transactions.
With all the ambition, this is not a task from the fieldpure theory. Several of the most productive Bitcoin Core developers, including Peter Wuille, Anthony Townes, Johnson Lau, Jonas Nick, Andrew Poelstra, Tim Ruffing and of course Gregory Maxwell, are working on a proposal for Schnorr signature support, which also includes support for Taproot - all within one protocol updates.
What is Taproot and how does it work?
P2SH
All bitcoins are essentially "locked" by scripts- a couple of lines of code included in the transactions recorded on the blockchain - that define how these coins can be spent in the next transaction. The terms of spending usually involve the provision of a signature confirming ownership of the coins. But other well-known conditions are possible, including, for example, temporary blocking (coins can be spent only after a certain block height or date) or multisignature (coins can be spent only if the transaction is signed with a certain amount from a given set of secret keys).
These conditions can be used in various combinations to create complex types of smart contracts. Here is an example of such a contract: coins can be spent if both Bob and Alice sign the transaction,orif after a week only Alice signs it,orif only Bob signs it, entering a secret code. Whichever of these three conditions is met first, the coins will be spent.
Since 2012 scripts (terms of spending)are often hidden initially; only the new owner of the coins knows how they can be spent. This is done using a trick called P2SH (pay to script hash), when initially only the script hash is written to the blockchain. This seemingly random number blocks coins. When spending these coins, the owner reveals both the entire script and its "solution". Anyone can then use the original hash to verify that the provided script is indeed the original coin-locking script and to ensure that the script's requirements have been met.
However, now when spending coinsit is necessary to disclose all possible conditions for their spending, including those that have not been activated. This has two major disadvantages. First, there is a significant amount of data, especially if there are many conditions. And second, it hurts privacy. In the public domain, information about all possible ways of spending funds is available, including, for example, wallet addresses and, possibly, even more.
MAST
MAST (Merkelized Abstract Syntax Tree) isA proposed way around these two shortcomings is through the use of Merkle trees, a compact data structure invented decades ago by cryptographer Ralph Merkle. In short, all the different conditions under which funds can be spent are hashedseparately(instead of being combined into a single hash) and organized into a Merkle tree, which ultimately produces a single hash: the root hash of the Merkle tree. This root hash “locks” the coins.
The unique advantage of this method is that when openedanydata from the Merkle tree, using the roothash plus some additional data (paths in the tree), one can verify that this particular data was included in the Merkle tree. The rest of the Merkle tree remains hashed and hidden.
That is, with MAST, only that condition can be expanded.spending that has been done. If in the example above Alice spends funds in a week alone, she will only reveal this activated condition (plus the path in the tree). No one will know that these funds could have been spent by Alice and Bob together, or by Bob alone, provided the secret code was provided. This makes MAST more data efficient than complex P2SH smart contracts and improves privacy.
However, when using Taproot and Schnorr signatures, you can achieve an even better result: to hide the very existence of the MAST structure.
Schnorr
Schnorr signature scheme has long been on the listpriorities of many Bitcoin developers and is currently under development for a likely deployment with the next soft fork. Many cryptographers consider the Schnorr signature scheme to be the best of its kind, because its mathematical properties provide a high level of correctness, it does not suffer from plasticity, and is relatively fast to verify.
Best known benefit in contextBitcoin is that Schnorr's “linear mathematics” allows signatures to be aggregated: multiple signatures in one transaction can be combined into one. A similar trick could be applied to multisig transactions. By combining both public keys and signatures into "threshold public keys" and "threshold signatures", multisignature transactions can be made indistinguishable from a regular transaction.
Moreover, the signature scheme can also be usedin more interesting ways. For example, you can use data to modify both the private and public keys. As a simplified example, the secret and corresponding public key can be modified by multiplying each by two. Multiplied by two, these keys will still match, and the x2 private key will still be able to sign messages that can be verified with the x2 public key. Anyone who doesn't know that the original key pair was changed won't even notice the difference; the modified keys look like any other key pair.
This opens up possibilities for using Taproot.
Taproot
Taproot builds on an interesting implementation: Regardless of the complexity, almost any MAST construct can (or should) include a condition that allows all participants to agree with the result and simply jointly sign the settlement transaction. In the example above, if Bob knows that Alice can independently dispose of the funds in a week, then he can cooperate with her now and sign the transaction together. (In many smart contract schemes, he will even be fined if he does not. Complexity really just ensures the integrity of the participants.)
Taproot resembles MAST andalwaysincludes a condition under which all participants can agree to spend the funds: perform a “joint close.”
This gets really interesting when using Schnorr signatures.
First, when you close together, you canuse the Schnorr "threshold" signature trick to make a transaction indistinguishable from the usual sending bitcoins from one user to another. In this scenario, the public keys of all participants are added together, resulting in a "threshold public key". The combination of signatures of all participants corresponding to this threshold public key - the "threshold signature" - allows them to spend funds.
So far so good, but spend money likethis is a normal transaction - this is the only thing they can do; structures like MAST are still excluded. This is where another feature of Schnorr signatures comes in handy.
All alternative ways of spending funds,in addition to joint closure, they are now combined into a separate script. This script is then hashed and used to modify the threshold public key. That is, instead of "public key x2" as in the example above, this results in "threshold public key x script". (We're still simplifying a little.) And this "threshold public key times script" corresponds of course to "threshold signature times script".
Now, if funds are spent together, then everyoneparticipants combine their signatures into a "threshold signature" and modify it using a script. The resulting "threshold signature multiplied by the script" allows them to spend funds. At the same time, which is important, to the outside world all this will look like an ordinary public key and an ordinary signature - an unremarkable transaction.
Only if it is impossible to jointly close the threshold public key can be shown as it really is: modified.
In this case, they are revealed asoriginalthreshold public key and script.This proves that the "threshold public key x script" was modified by this particular script. Thus, as with P2SH, the network receives proof that the funds can be spent if the alternative conditions outlined in this script are met. (And, as with P2SH, these conditions are, of course, immediately met for the funds to be spent.)
It is also possible that, instead of a script,to modify the threshold public key, the root hash of the Merkle tree is used, which includes all possible conditions for spending funds: a MAST structure. That is, in order to spend funds, it is necessary to disclose to the network only the condition that was activated.
Thus, Taproot offers all the benefits of MAST, while under normal circumstances no one would ever know that a complex smart contract was hidden behind a simple transaction.
</p>