
I've spent most of the past year working on energy projects at ConsenSys, culminating inoffshoot aiming to become the world's firstblockchain-based energy system called Grid+. Our priorities include creating a new system architecture that will allow unsophisticated users to safely store and use cryptocurrencies. Through my work, I have also had the opportunity to interact with a number of people and large organizations entering the crypto space, who inevitably come to the same question: How to store cryptocurrency? What is the safest and most convenient way to handle cryptocurrency? Best answerpresently– probably a hardware wallet.The most popular wallets on the market right now are Trezor and Ledger Nano S. There are other wallets, such as KeepKey, but these are essentially modifications of Trezor. I took apart the Ledger Nano S and Trezor wallets and want to share the results, as well as important conclusions about security.
</p>This includes my opinion of where I see largeattack surface, but I don't necessarily know or imply any particular hack. In addition, I have not considered devices without their own display due to the significantly increased vulnerability to attacks.
Iron
Trezor
Trezor is a relatively simple deviceconnecting via the Micro-USB connector. It has a very simple molded plastic body with two plastic buttons and an LCD display. Interestingly, the plastic case is glued with something like cyanoacrylate or superglue.
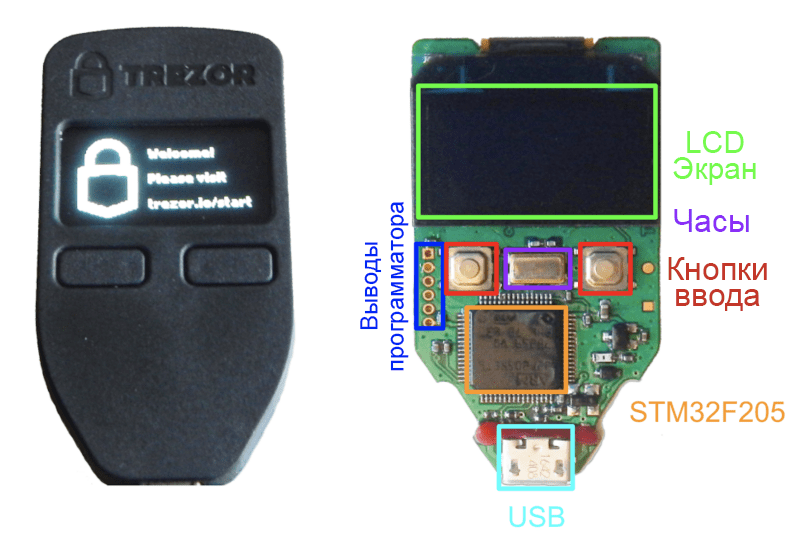
Trezor — appearance and printed circuit board
Trezor usesonlymicrocontroller – standard STM32F205, – whichcreates a large hardware attack surface. This is a very common 32-bit ARM Cortex M3 processor. It is not considered one of ST's secure microcontrollers and does not use Secure Enclave technology. This general purpose microcontroller generates and stores private keys. For these reasons, Trezor is not certified according to the general security criteria.
Ledger nano s
Ledger Nano S also connects via Micro-USB,has two input buttons and a display. The main difference between Trezor and Ledger is that the latter uses not one, but two microcontrollers: STM32F042K and ST31H320. The STM32F042K is very similar to the STM32F205 used in the Trezor, but it has an internal clock rather than an external one. Also interesting is that Ledger has a full bank-grade microcontroller with Secure Enclave ST31H320 technology, where the wallet's private keys are stored. The ST31H320 has already found many other uses, including banking, identity and pay TV. In addition, it meets safety standards according to the general criteria for the EAL6 + level. The ST31 / STM32 combo architecture has a lower but decent EAL5 + certification. In addition to storing private keys securely, the Secure Enclave can store the device key, which provides a high degree of confidence that the Ledger device is not fake or compromised on its way to the user.

Ledger Nano S and PCB
Comparison
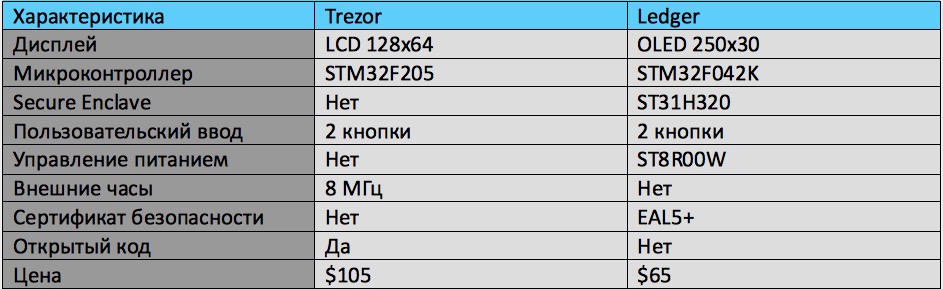
Hardware comparison of Trezor and Ledger
Potential vulnerabilities
Coming to an overview of what I believethe relative vulnerabilities of each system, I will describe some basic assumptions about what might happen. The first assumption is that the computer to which the hardware wallet is connected may or has been compromised in some way. I will not go into exactly what mechanism or what kind of malware is used to hack the device, but I will just assume that it is possible. Second, I will also look at ways of stealing funds, assuming that an attacker can take over a device before or after user initialization. I think the above assumptions are a good starting point because the purpose of hardware wallets, at least in my understanding, is to help mitigate security vulnerabilities on the assumption that these assumptions are correct. Also, if we drop the assumption that the wallet is connected to a compromised computer, there is no need for a hardware wallet, because you can just use the computer.
Middleman attack for $ 800
Even though the Ledger Nano S has a display,it is still vulnerable to middleman attacks. The reason is that it only shows 8 digits of the recipient's address. Confirming such an 8-digit transaction can be circumvented at relatively low cost. Also note that the display of the 8-digit recipient address applies not only to Ethereum, but also Bitcoin and Litecoin.
Correction: The latest firmware 1.3.1 shows full Bitcoin addresses, so this does not apply to devices withthe lastfirmware andthe lastversion of the Ledger Bitcoin Wallet application forBitcoin transactions. However, for Firmware 1.3.1 and Ledger Ethereum Wallet 1.0.19, only partial (8-digit) Ethereum addresses are still displayed, andthis vulnerability still exists.

Ledger transaction verification
Current cost of generatingthe 8-character address register on the vante.me custom address generator is approximately $ 800. Although vante.me is designed to create addresses that start with human-readable text to make the address more recognizable, the computational cost of splitting a string into 4 given characters at the beginning and 4 at the end is the same.
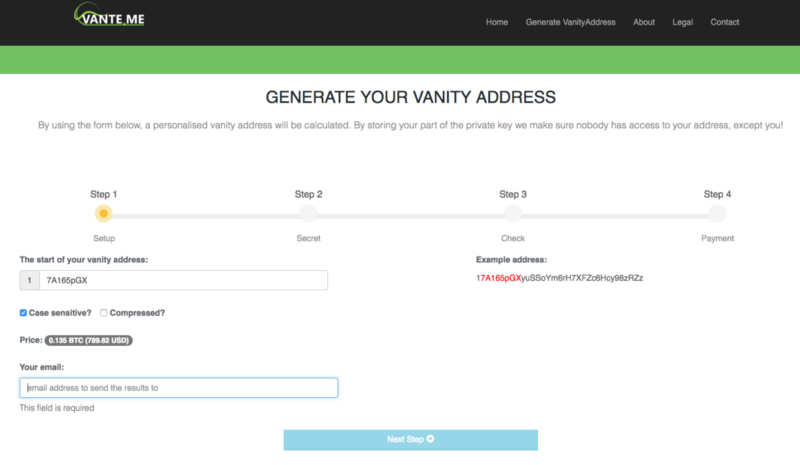
The cost of generating an address on vante.me
Thus, if you connect the Ledger Nano Sto a compromised computer and will regularly use it to transfer large amounts to one or more accounts, you are vulnerable to this attack. For example, let's say you have an exchange account where you transfer money regularly. If your computer is compromised, the attacker will know to which addresses and how much money you usually send. The attacker can then expend the computing power needed to create addresses that appear identical (8 matching characters, $ 800 per address) or nearly identical (7 characters instead of 8, $ 30 per address) and wait until you create the next large transaction. When your connected Ledger needs to confirm a transaction using your account, it can override it with its own account, and you won't guess anything by confirming the transaction on the device.
Interestingly, Trezor is not vulnerable to such an attack,because it displays the complete address of the recipient on its display before confirming the transaction. It also sheds light on an interesting detail: before sending a large transaction, you need to check at least 10 characters (cost of attack ~ $ 3.1 million) of the address (preferably the entire address). I also want to mention here that a middleman attack can be prevented by using disposable addresses to send money from Ledger. This assumes that the attacker will not have enough time to generate a fake address between the discovery of the recipient's address and the user sending funds.

Confirmation on Trezor
Updating the firmware of a USB device
Ledger and Trezor are updated with somethinglike a USB Device Firmware Upgrade (DFU) for ST microcontrollers. USB DFU allows you to update device firmware via USB port and device manager on a connected computer. Unfortunately, there are a number of potential attack vectors associated with the ability to remotely write firmware over USB.
There have been a number of successful attempts with oneonly DFU can remotely unload the memory of the STM32F microcontroller family. What does this mean? This means a lot to Trezor, because it potentially allows a hacker to remotely extract private keys from the device. For Ledger, this is not such a big problem, because the keys are not stored on STM32, but on ST31 with Secure Enclave technology. Thus, even if the STM32 memory is copied remotely, the private keys remain safe on the ST31.
Beyond providing potentialremote unloading of STM32 memory, USB DFU could potentially allow an attacker to write malicious code to the device during the update. Although Ledger and Trezor display the checksum on the device's display during the update, it can easily be falsified using malicious code. For this to potentially work, your computer must be jailbroken at the same time that your wallet firmware is updated. If Trezor was updated with malicious code, the attacker could actually gain control of the funds. In the case of Trezor, it is enough to reveal the private keys. In the case of Ledger, the keys will not be revealed and the cracker will not be able to create malformed transactions due to the Secure Enclave.
Bypass PIN codes
The next series of vulnerabilities that I would like toask about what could happen if a hardware wallet falls into the hands of attackers. Trezor and Ledger have a reset option in case of entering an incorrect PIN 3 times. This prevents an attacker from taking over the wallet and using a brute force attack to determine the PIN.
Funds are safe because they are PIN protected, right?
At DEF CON 25 there was a presentation where Cryptotronixdemonstrated that the STM32F205 Trezor can be triggered by a voltage fault or a clock fault. This creates vulnerabilities in Trezor, allowing a hacker to obtain private keys without having to know a PIN. There is even a blog with step-by-step instructions on how to do this without any special hardware, also promising to publish the source code in the future.
What about Ledger?Ledger is less vulnerable to such an attack thanks to its internal clock as well as the Secure Enclave. If everything is foreseen in Ledger, Secure Enclave will require the device PIN before the device confirms the message. Thanks to this, funds will not be able to be stolen from the Ledger even in the case of a successful attack on the STM32F042K.
Supply chain
Physical mechanisms of "security" of devices,seem to be relevant to Trezor due to the potential attack vectors associated with hacking a device in the supply chain. In addition to the superglue that is used to seal the case, Trezor's packaging is "sealed" with holographic stickers, which also seem to be an attempt to protect against tampering. The efforts made by the manufacturer to ensure Trezor will not be hacked before being received by the end user should be alarming. Trezor adds these "security" measures for the reason that it cannot guarantee that a new device ordered through its website is the same device that it has created and programmed.

Trezor packaging with security hologram
If an attacker manages to intercept Trezor beforeif received by the end user, he would be able to open it and use the conveniently provided outputs for the programmer to write malware onto the Trezor. This is further aided by the fact that all Trezor firmware is open source. Additionally, since the Trezor device key is stored on the STM32, an attacker can also replace the key after flashing the device. This way, even the manufacturer will not be able to find out whether the device is hacked or whether it is even counterfeit.
Ledger doesn't have such problems because SecureEnclave is able to secure the device key that Ledger uses to prove its authenticity. This significantly reduces the possibility of fake or compromised devices entering the supply chain.
Recovery phrase
The most vulnerable piece of the security puzzle isthis is probably a recovery phrase. A recovery phrase is a set of 12-24 words that allows you to recover private keys using BIP39. Unlike hardware wallets, which provide some barrier to abuse or hacking, the recovery phrase is plain text. Grid + describes this vulnerability as a "sock drawer" attack, as many people have probably hidden their recovery phrase in a sock drawer at least once.
This is probably the main vulnerability of the hardwarewallet. It is also especially ironic that if someone wants to secure their recovery phrase, they may have to use a bank safe. After nearly a decade of labor to create distributed peer-to-peer money, the recovery phrase takes us back to where we started when we kept money in the bank. This further underscores the fact that cryptocurrencies are a bearer asset. As with gold, their safety, at least for now, depends on the user's ability to physically secure them or hide their location.
There are ways to improve the security of a phrasefor recovery, such as its separation and storage with several trusted counterparties. The recovery phrase can also be encrypted or used in combination with a passphrase.
Surveillance
The last thing worth considering at least briefly isIs the idea of surveillance. If an attacker manages to get the PIN from your hardware wallet, anything is possible. There are remote surveillance mechanisms when a computer's webcam can be turned on and viewed without the knowledge or consent of the user. There are also more direct methods of surveillance where a hidden camera may be installed where you live or work. Edward Snowden was clearly paranoid about the surveillance, as can be seen from the fact that he used a blanket to hide the password entered. This may not be the most likely threat, but if there is sufficient motivation and the target is known, then this is perhaps the simplest attack vector.

Edward Snowden - From Citizenfour. Snowden's Truth "
Let's summarize
What conclusions can be drawn from the above?Below is a summary of the potential Trezor and Ledger vulnerabilities. If it weren't for the vulnerability to middleman attack, Ledger would have emerged as the clear winner. However, this problem complicates any solution. If Ledger had listened to community feedback and included the full recipient address, or at least 10-11 characters, instead of just 8 characters, then I would be much safer to call this device the best.
BTChip (Ledger) recently announced an update to the wallet app to display full addresses. Once that happens, I'll recommend Ledger as a better choice than Trezor.
Comparison of vulnerabilities

Is there anything else you can do to increasesecure storage of cryptocurrencies? Yes. Multi-signature wallets. Multisignature wallets allow you to transfer funds only after confirming a transaction n of m keys. In its simplest form, it is 2 of 3 keys. In the case of Bitcoin and its derivatives (such as Litecoin), this is exactly how I recommend storing institutional funds. The technology is mature, has a long history of success, and both Trezor and Ledger offer some form of multi-signature support. In addition, the need to confirm a transaction by multiple people before money can be transferred creates the internal controls typically desired by a company.
Unfortunately, Ethereum does not yet have a built-insupport for multi-signature wallets. Any multi-signature Ethereum wallet is based on a smart contract, and this smart contract can have vulnerabilities, as recently happened in the case of the Parity hack. Therefore, if we talk about Ethereum, I advise you to wait for the implementation of EIP86 before using multisignature to securely store Ether or ERC20 assets.
We hope that as soon as it appears on the marketGrid + agent device, it will be possible to safely store cryptocurrencies online. Until then, be vigilant and remember that we live and work in an insidious environment. There are no perfect solutions, and we advise all users to inquire about the advantages and potential disadvantages of all existing solutions.
</p>


