Blockchain is considered to be a secure technology. Payments cannot be faked and transactions cannot be reversed.But due to some technical features, evenSuch a seemingly reliable system has vulnerabilities. The threat lies in attacks on the network, the most dangerous of which is an attack (51%). However, in the case of Bitcoin, its organization is extremely expensive and is considered unprofitable.
However, there are other, less costly attacks,which can cause huge damage to individual users. One of them is a “dust attack” (Dusting Attack). It allows you to reveal the identities of the owners of cryptocurrencies, and at the same time helps to freeze transactions and increase commission fees on the network.
There are suspicions that such an attack on the Bitcoin networktook place quite recently - on November 15, when the mempool reached its highest load in a year and a half. What was it? What exactly is a dust attack dangerous and how does it work? What cases are known to the market and how to protect yourself?
What happened on November 15th?
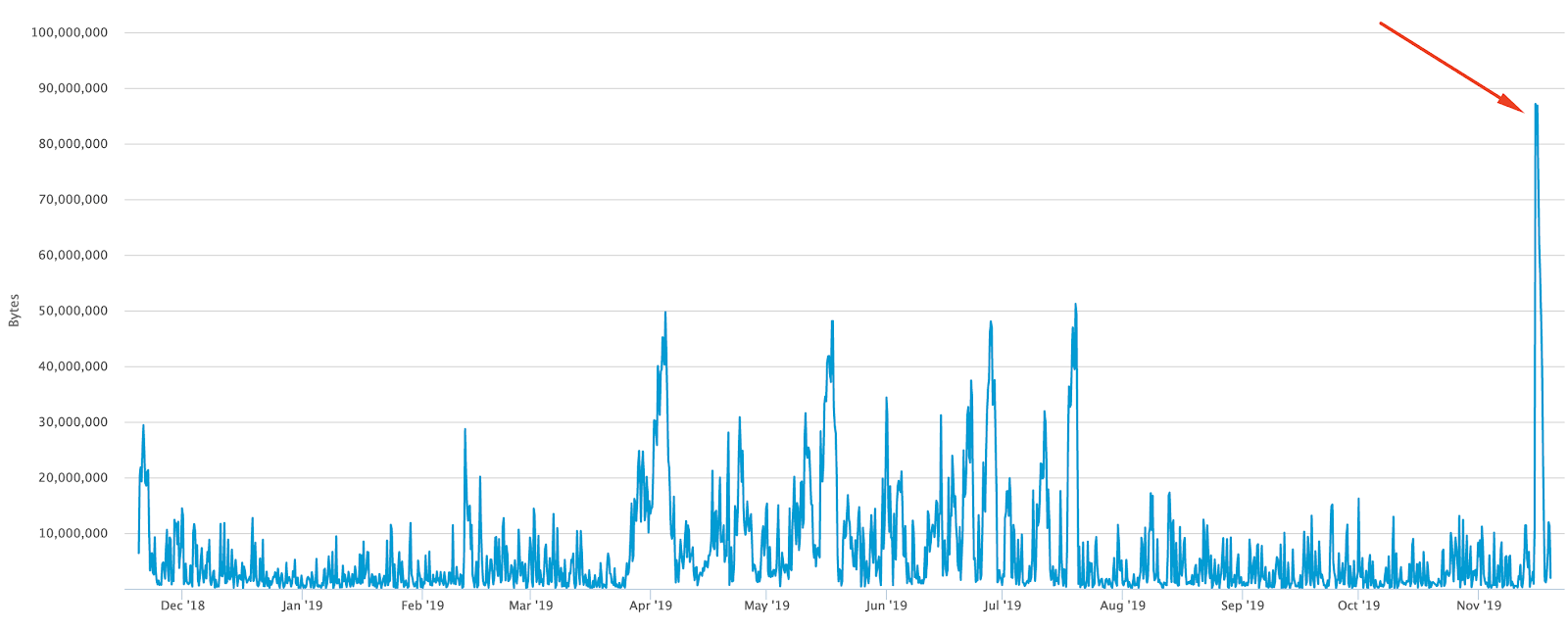
On Friday, the Bitcoin mempool (the place whereunconfirmed transactions) began to fill at an abnormal rate. For the first time in almost two years, its size exceeded 90 MB. The last time such a high load was observed was in January 2018, when the crypto community was trying to recover from December 2017.
During the current month, the size of the mempool never,with the exception of the described case, it did not exceed 12.6 MB - this is about seven times lower than the Friday mark. Usually a heavy mempool means that there are a lot of frozen BTC transactions in the network, but this time it was different: the number of operations did not always reach 20,000.
This means the mempool has been cloggedfew but heavy transactions consisting of several transfers at the same time. The bulk of them contained extremely low amounts, including transactions with 1 satoshi (0.00000001 BTC). The commission in such transactions was set at a low level, so the average level of commission fees did not increase, and the transfers of ordinary users did not get stuck.
Why it all happened this way and who is behind it is not known, but there are assumptions. So, CEO of Bitrefill Sergey Kotlyar suggested that this was just “autumn cleaning” of one of the large companies.
On the mempool today. Someone is cleaning up 100 MB of bitcoin transactions in their wallet. These are all at low fee and not causing any disruptions anywhere. Business as usual, just someone somewhere doing much needed a fall cleaning, nothing to worry about. pic.twitter.com/nzNJi25emI
- Sergej Kotliar (@ziggamon) November 15, 2019
«This is what the mempool looks like today.Someone is clearing 100 MB of Bitcoin transactions from their wallets. They are all low commission, so they won't cause any disruptions. Business as usual, just someone somewhere doing autumn cleaning. There's nothing to worry about.
And here is the CEO of the Australian crypto portalNuggetsNewsAU Alex Saunders dug deeper, suggesting that none other than the Binance crypto exchange does this. In his opinion, this is how the exchange gets rid of small balances of BTC and USDT.
#Bitcoin cleared 90mb of transactions over the weekend. @binance cleaning up $ BTC dust or $ USDT accounts I believe. All at min fee of 1 sat / byte. ?? pic.twitter.com/K75oUf3SSQ
- Alex Saunders (@AlexSaundersAU) November 17, 2019
«90 MB of transactions passed through the Bitcoin network over the weekend. I think this is Binance collecting balances from their BTC or USDT accounts. All this with a minimum commission of 1 sat/byte.
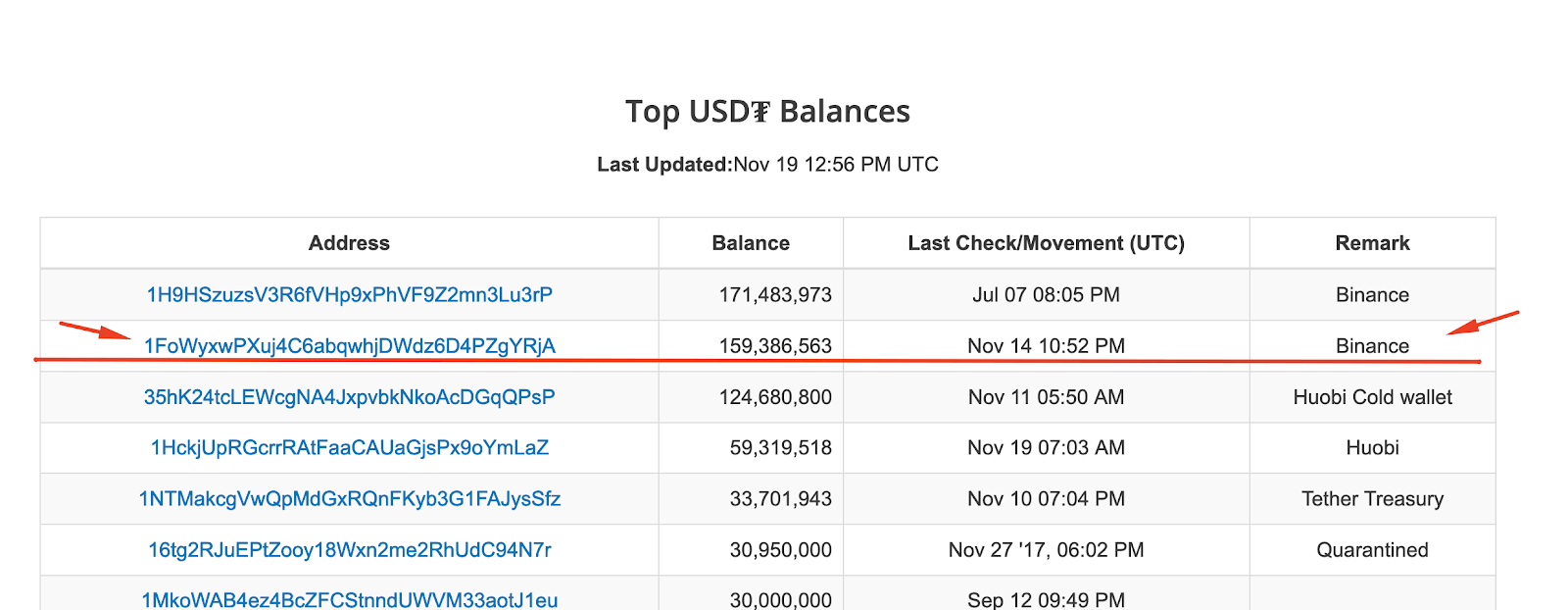
Another, less well-known crypto expert under the nicknameFrank Topbottom even tried to prove Binance’s involvement. Thus, one of the addresses marked on November 15 is 1FoWyxwPXuj4C6abqwhjDWdz6D4PZgYRjA. The exact same address, only USDT, not BTC, is assigned to the exchange in the list of the richest Tether wallets.
Since Tether is based on the Omni platformLayer, which in turn works on the Bitcoin blockchain, then small bitcoin transactions are made during USDT transfers. Therefore, the crypto enthusiast suggested that the first cryptocurrency mempool owes its load to USDT transfers from Binance.
However, again, what really happened -No one knows. Some experts do not rule out that at this time the Bitcoin network was subjected to a carefully planned “dust attack”, due to which both large crypto companies and ordinary users could suffer.
What is a dust attack?
Dusting Attack on Bitcoin Network -This is one of the “white” ways to negatively impact the cryptocurrency network. Her organization does not require billions of dollars in costs and does not need to be a coding genius.
How exactly does it work:
- Attackers spread many small transactions on the Bitcoin network.
- The amount of transfers is extremely small - from one to several thousand Satoshi. In bitcoins, it is from 0.00000001 BTC to 0.00005000 BTC, in dollars - up to $ 0.04.
- Because of such a tiny size, such amounts are called "dust" - hence the name of the attack.
- Moreover, the commission paid is quite adequate and often turns out to be more than the amount of the transfer.
- Coins go to the addresses of various network users. Those, in turn, often do not even notice them, since visually the balance practically does not change.
Conclusion: A “dust attack” is when attackers send many small transactions to various network users.
Well, we figured it out. But why is this needed? What is the use of sending someone your coins? There is a rational reason for this, and not even one.
First reason: spam attacks on the network
Despite the fact that from the outside there is a “dust attack”looks more like an airdrop; in fact, it is a well-planned fraudulent campaign. One of its goals: to “spam” the blockchain, causing transactions to freeze and fees to increase.
How exactly does it work:
- Dust transactions along with all the others are stored in the mempool pending confirmation by miners.
- The more spam transactions in the mempool, the longerordinary users have to wait for confirmation and set a higher commission, since transfers with a high “fee” are processed first.
- If the “dust attack” is not carried out with a mediumand with a high commission, miners initially process spammers’ transactions, and ordinary crypto enthusiasts have to wait for confirmation for hours, days, or even weeks. The only way out is to set abnormally high commissions.
- A spam attack is carried out in order to discredit the network or slow down / disrupt some transactions.
Conclusion: a “dust attack” spamming the blockchain with unnecessary transactions, causing freezes of transfers and an increase in commission fees.
This method has been very popular for several years.back when bitcoin was not worth so much and network commissions were lower. Now this venture is too expensive, and dust transactions rarely include large fees.
Second reason: identity disclosure
The trend towards spam in the cryptocurrency network is graduallyis fading, but “dust attacks” do not lose popularity because of this. In recent years, attackers have changed their focus: they now use tiny transfers to reveal the identity of address owners, and then launch phishing attacks or blackmail the victim.
How exactly does it work:
- Crypto wallets allow you to generate addresses foreach new transaction based on the same seed phrase. This makes it difficult to determine the owner of a specific address. But there is a loophole.
- The fact is that technically the total balance on the wallet consists of the sum of “unspent outputs” (UTXO). Surprisingly, this works exactly the same as in the case of cash.
- If you have 1000 rubles, this is far from alwaysmeans that you have 1000 rubles in one bill. This can be several bills of different denominations: one for 500 rubles, three for 100 and twenty for 10. Similarly, with cryptocurrency wallets: with a total balance of 1 BTC, you can actually have “unspent outputs” of 0.7 BTC, 0.2 BTC and 0.1 BTC.
- Suppose you need to spend 0.99 BTC, but you don’t have an exit specifically for this size. Therefore, when creating a transaction, the wallet will go to a technical trick and combine all your "unspent outputs" into one. He will generate a new address and create a transaction for 1 BTC, including 0.01 BTC “change” in it. This amount will automatically return to you and become your new UTXO.
- The addresses from which all UTXOs have been spent are no longer used, but remain valid for accepting coins.
- This is right for the attackers: they send a tiny fraction of bitcoin to specific addresses. As a result, new UTXOs appear in the wallet, which sooner or later mix with others and go from a new address.
- The attacker simply tracks the movement of the coins he sent and establishes a connection between the addresses. This way you can identify an influential company, a Bitcoin whale, or an anonymous expert.
- The information received is used to carefullyplanned phishing attacks, cyber crimes, blackmail, and other targets. The same method can be used by police to identify the offender or special services for tracking people.
Conclusion: using a “dust attack”, the connection between addresses is analyzed in order to find out who operates the cryptocurrency.
What cases are known to the market?
If the “dust attack” were not effective, itswould not have been carried out. But we see how at different times cryptocurrency blockchains are faced with its unpleasant consequences. Recall some well-known cases:
- Spam attacks on the Bitcoin network after the launch of BitcoinCash in 2017. Two years ago, Bitcoin Cash was born - the favorite brainchild of Roger Ver, which he positions as the true Bitcoin. A few months after the launch, the network of the first cryptocurrency several times became a victim of “dust” spam transactions with high fees. This led to freezing of transfers and an increase in recommended commissions (at one point the figure jumped above $30). The promotion was repeatedly accompanied by Bitcoin Cash pumps. According to many crypto activists, Roger Ver himself was behind those “dust attacks”, wanting to clearly demonstrate the advantages of Bitcoin Cash over Bitcoin.
- “Dust attack” on the Bitcoin network in October 2018.At the end of last year, the creators of the Samourai Wallet crypto-wallet recorded a flow of suspicious small transfers on the BTC network. The developers immediately released an updated version of the software, which made it possible to automatically record “dust attack” transactions and impose a ban on their spending.
- “Dust attack” on the Litecoin network in August 2019.In the summer, a Charles Lee coin became the victim of attackers. Unknown people began sending tiny transactions to users and crypto companies, including the Binance exchange, in order to de-anonymize LTC addresses.
How to protect yourself?
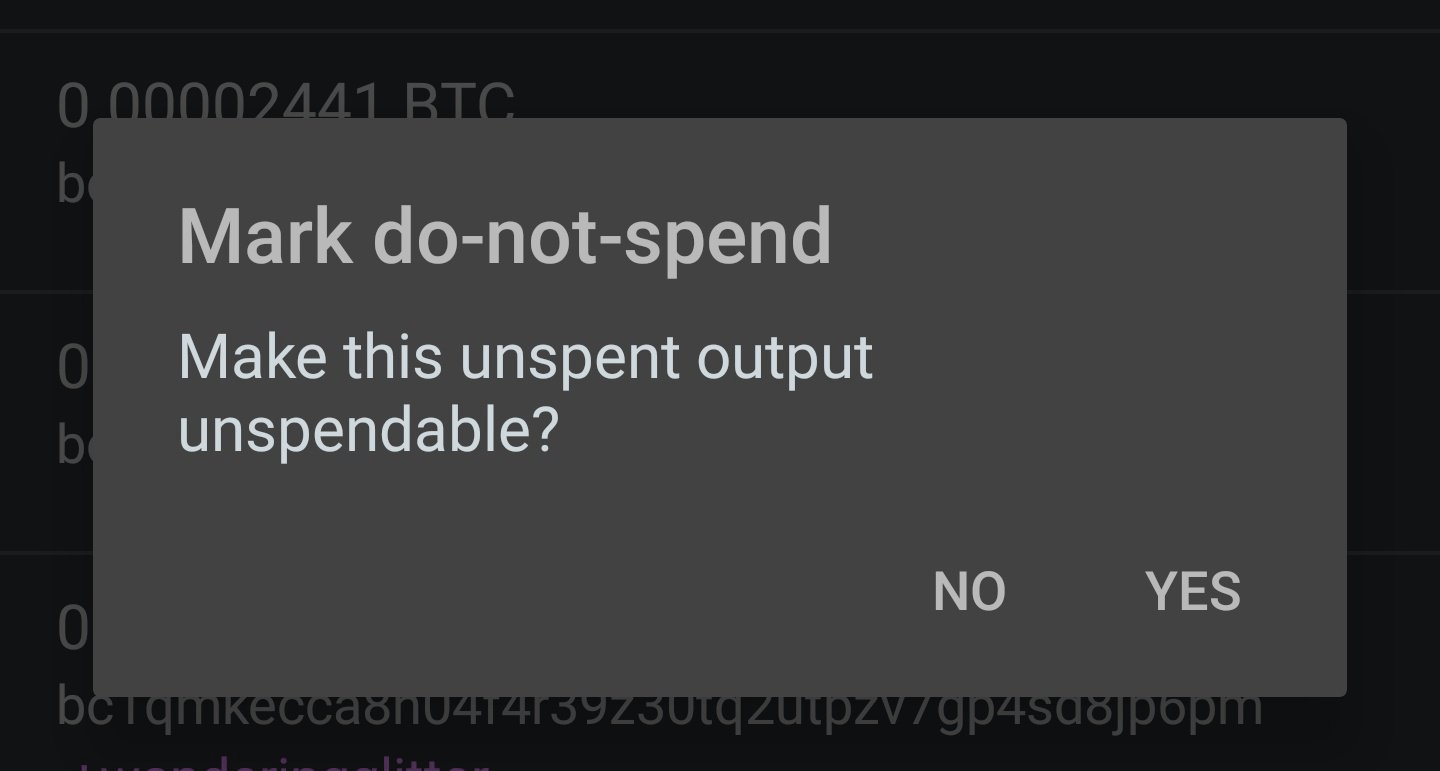
The only way to reliably protect againstconsequences of “dust attacks” - do not use the received coins. You just need to prevent them from being mixed with other assets. Then the attacker will not be able to identify the connection between your addresses. That is, the UTXOs obtained as a result of the “dust attack” simply need to be “frozen.” Unfortunately, not all wallets provide this opportunity.
The function mentioned above works most convenientlySamourai Wallet, which is also recommended by Binance specialists. Let us remind you that it allows you to mark small incoming transfers and not use the received digital money in the future. In the main Bitcoin Core wallet, this is implemented less conveniently: you have to select the UTXOs used when forming a transaction. You can also freeze coins through Electrum, but this wallet is not particularly secure.
</p>