Roskomnadzor has taken up the study of anonymous and decentralized networks that allow you to bypassdepartment locks. The ultimate goal of this study is to restrict access to them at the legislative level.
The Tor browser, the Telegram Open Network platform, and a number of other networks based on anonymous secure connections are at risk.
Terms of Reference by ForkLog on Scribd
The work is entrusted to the federalResearch Center "Informatics and Management" at the Russian Academy of Sciences. 9.2 million rubles will be allocated to specialists and the deadline for preparing the report is June 30, 2020.
ForkLog figured out the reasons for the popularity and principles of the Tor browser, and also assessed the reality of the threat to the anonymous Internet from the ILV.
Stop. Blocking Tor, Telegram… It seems like this has already happened?
An attentive reader will recall that from November 2017For years, a law has already been enacted in the Russian Federation that obliges owners of so-called anonymizers to block access to prohibited sites. Telegram messenger has been blocked in the country by a court decision since April 2018 - another issue, which is unsuccessful.
According to the head of a public organizationRosKomSvoboda Artem Kozlyuk, the law on anonymizers was needed to force various proxy and VPN services to cooperate with the Russian authorities and to provide ILV with the possibility of blocking them in case of refusal to filter traffic.
«This law until todayis practically not applied, despite the fact that it came into force more than two years ago. The only thing is that in March 2019, Roskomnadzor sent a notice to ten large VPN services with a requirement to connect to the registry of prohibited sites. Then all services, except Kaspersky Secure Connection, refused, but Roskomnadzor did not take any measures against them»,- said the expert.
The current study, according to Artyom Kozlyuk, is being carried out as part of the implementation of the “sovereign Runet”.
«The Center under Roskomnadzor wants to studyspecific technologies that are difficult to block directly or hack, as they are cryptographically secure. In order to, based on the analysis carried out, draw up technical specifications for the implementation of hardware and software systems for filtering traffic or “jamming the signal”, if in principle there is such a possibility»,he added.
Such an approach is fraught with the fact that the blocking process will become opaque, the expert warns:
«If RKN is under controlIf there is some equipment that allows you to identify and limit some type of traffic, then there is no need to maintain a separate register of prohibited sites and upload this data to telecom operators.
Perhaps lists will existin parallel, but at the same time no one will know why this or that service suddenly stopped working, which «affect» restricting access to some protocol or signature. If Roskomnadzor carries out this practice of off-registry blocking, even more confusion will arise.
The head of «RosKomSvoboda» also big questions, because the idea of the RKN is quite non-trivial.
«I'm not sure we'll feel it anytime soonmonths, or even years. We can feel individual elements quickly. Most likely, the switch that the RKN was given under the law on the sovereign Internet will be used in the event of mass unrest in any regions, and we will see a large number of regional shutdowns.
In RKN itself, the new tender is explained by the desire to findability to block prohibited information. The list of technologies under study, according to the document, will include the Invisible Internet Project (I2P), The Onion Router (TOR), Telegram Open Network, Freenet, Zeronet, anoNet, as well as mesh networks Yggdrasill, cjDNS, Briar, Signal Offline and FireChat.
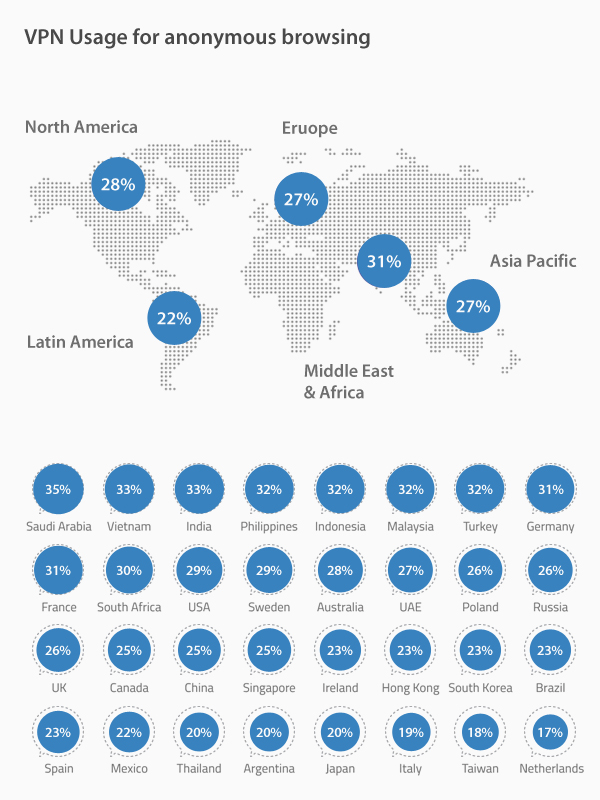
At the same time, not a word is said about VPN technology, which, according to GlobalWebIndex service, is used by a quarter of Russians.
This was noticed by the ex-director of special areas of one of the Telegram structures Anton Rosenberg.
“The technical assignment lists a large listtechnologies and protocols that need to be analyzed. Not all of them are popular, not all are used to bypass locks. It can be assumed that they were added because the compilers of the document themselves did not very well understand what and how it works, either to blur, cover up any specific points of real interest to the customer, or simply to create the appearance of a large and complex work, so that justify the allocated amount of funds ”,- he said in a comment to Kommersant.
How is the Tor browser different from other browsers?
Tor is an overlay network that isa kind of «overlay» some additional structure on top of the existing Internet infrastructure. Thus, it provides broader capabilities not originally provided for by the developers of classical network protocols (TCP/IP).
According to a Tor Project employee and messengerSignal by Diana Azaryan, Tor's core value lies in the browser's original purpose - «Internet users should have private, uncensored access to the web»:
«A huge international team is working on Tora community made up of volunteers who are dedicated to protecting human rights. Tor has become the world's most powerful tool for ensuring privacy and freedom on the Internet.
Bypassing locks in this regard appears as a side effecteffect, continues consultant «RosKomSvoboda» Leonid Evdokimov. The Tor network is built in such a way that it is not possible to distinguish between users and does not collect their personal data.
«The network cannot «hang» onuser has a shortcut with blocking lists, since it is unknown what country he is from and the laws of what jurisdiction he must obey. Therefore, filtering is left to the «output nodes», in accordance with their local legislation»,- explains the expert.
Another useful feature of Tor is the impossibility of retargeting, that is, re-displaying ads.
«Anonymity in the era of ad network surveillanceuseful when buying gifts for close relatives. Imagine that you are choosing a gift for your wife/husband, and a few hours later your domestic partner shows an advertisement for this gift. This situation can kill the whole surprise, and Tor can help prevent it.- adds Evdokimov.
And although anonymity and privacy are the main features of the Tor browser, they are not absolutely guaranteed, says Stanislav Shakirov, technical director of RosKomSvobody.
«Using Tor, you can de-anonymize,for example, if you access social network accounts through a browser. There are also a lot of other options for calculating the user, for example, timing [that is, through the time of entry and exit to the network - ForkLog note]».
Why is the Tor browser audience growing?
Russia is in second place in terms of numberTor users, after Iran. Over the past year, a little more than 330 thousand Russians used the browser daily, which is 17.39% of the total number of users.
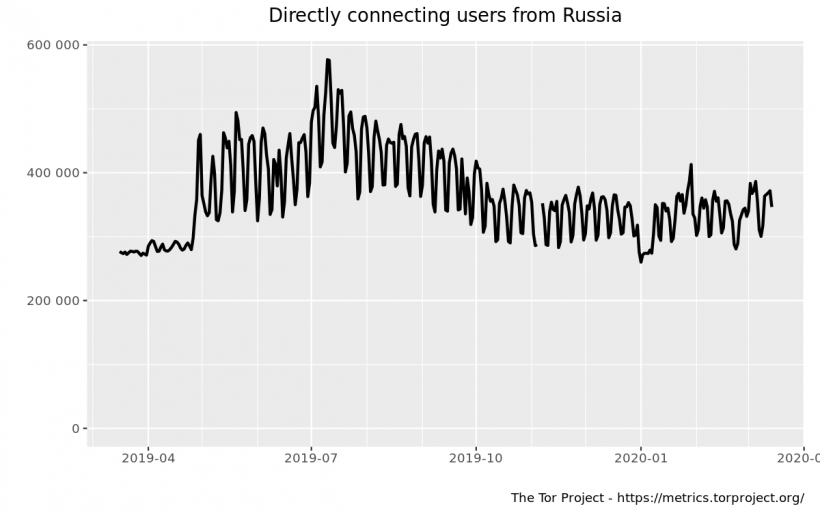
However, it’s still ten times less thannumber of Telegram users. According to the research company Mediascope, in August 2019, the daily Russian audience of the Telegram mobile application approached 4.4 million people.
Most of the Tor traffic in Russia is Hydra darknet marketplace traffic, says Ksenia Yermoshina, Center for Internet and Society CNRS and Citizen Lab research fellow.
«The reasons for the growth of the Tor audience may beare associated with the blocking of popular services or with the popularity of platforms that are located in the .onion domain (the same Hydra). If the number of arrests of people for reposting or publishing increases in a country (and the identification of the authors of such posts often occurs by IP address), there is reason to assume an increase in Tor users.— she said in a comment to ForkLog.
At the same time, high-quality VPN services can easily entice Tor to an audience whose goal is to bypass blocking or maintain anonymity by changing the IP address.
«VPN is usually more convenient, faster, fewer problemswith watching videos and other multimedia content. If people find out about a good VPN, many would rather switch to it than sit on Tor. This is especially noticeable in the example of journalists, for whom connection speed and the ability to open videos and photos are important. They need javascript, which is disabled by default in Tor. Therefore, if there is an option for the editors to provide licenses for VPN or a good free/cheap VPN (for example — Psiphon, PIA) - then they will prefer VPN»,— concluded Ksenia Ermoshina.
Are Roskomnadzor’s threats to block Tor real?
According to Diana Azaryan, Tor lock is quitefeasible, as the experience of several countries proves. In September 2009, the PRC authorities, using simple IP blocking, blocked the public list of repeaters and directories of the Tor browser - about 80% of public network nodes were censored.
In 2012, Iran and China began to use DPI (deep traffic filtering system) to block the Tor Project network. There have also been locks in Kazakhstan and Ethiopia.
However, even in the event of a lock, the Tor network will continue to operate.
«Users will still be able to connectto the network through bridges - non-public nodes. Even if the network blocks the main Tor Project site, you can get bridges in other ways. You can also use the technology «Connected Transport» (Pluggable Transports), which masks traffic, making it indistinguishable from «normal»/allowed traffic»,— said Diana Azaryan.
According to her, there are several types of interchangeable transports that follow a single specification. For example, meek transport was created specifically for residents of China.
The simplest way to restrict access toTor browser will block bootstrap nodes - special «hardwired» into the program of the address from which «is loaded» the initial configuration for the operation of the overlay network program, continues the consultant of RosKomSvoboda. Leonid Evdokimov:
«With some degree of success it canblock both Tor, I2P, and DHT torrent clients. And this will all work well until clients for overlay networks begin to actively «resist» blocking».
At the same time, he recalls the sad consequences of «blocking» RKN:
«Any threat can be realized, questiononly in the amount of collateral damage. And Roskomnadzor is not very worried about the latter - we already saw this in April 2018, when, in an attempt to block Telegram, the department also blocked Google and many Amazon networks, breaking the functionality of Slack, Ted.com and millions of other sites.- says Evdokimov.
Given that ILV was involved in the studyThe Academy of Sciences - there may be temporary successes in blocking the Tor browser on the territory of the Russian Federation, but in general the threat is illusory, believes the representative of the Internet Protection Society Alexander Isavnin.
«Overlay networks are evolving significantlyfaster than they can be blocked. They will reorganize their work and the results of their «research» will become irrelevant, blocking will stop working. In addition, a 9 million budget by Russian standards is nothing, normal research cannot be carried out on them»,— the expert summarized.