Blockchain addresses associated with Eastern Europe have the second highest level of participation in illegal activities.activity, second only to Africa, - shows the study Chainalysis.
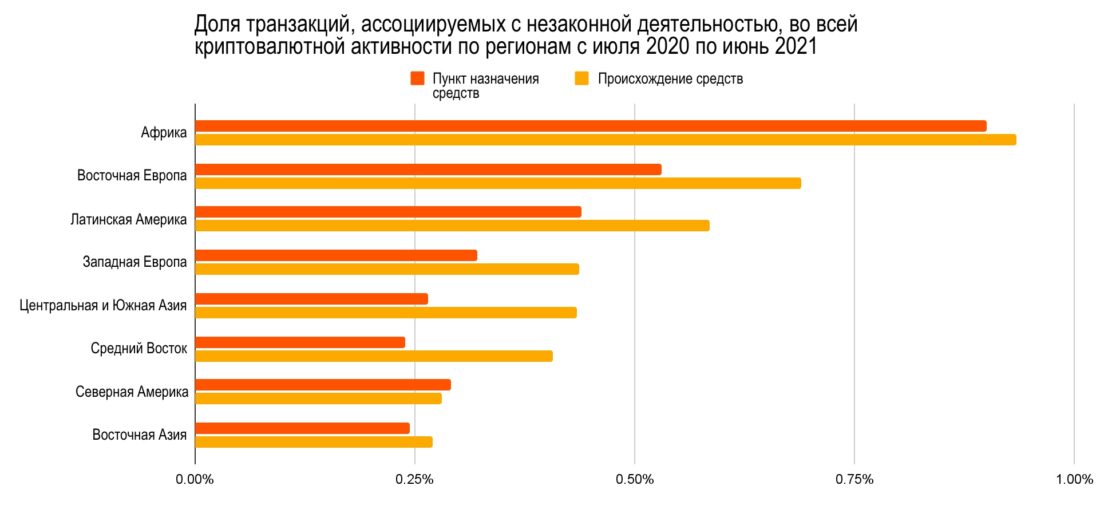
It is worth keeping in mind, however, that the total volumeEastern Europe has a much larger cryptocurrency economy than Africa, as does Latin America, the region with the third-highest rate of involvement in illicit activity. In fact, Eastern Europe is the only region with a total transaction volume of $400 million or more for which illicit activity accounts for more than 0.5% of the total value of cryptocurrencies sent and received.
In terms of the net worth posted toFor cryptocurrency transactions to addresses associated with illegal activities, Eastern Europe ranks second, behind only Western Europe.
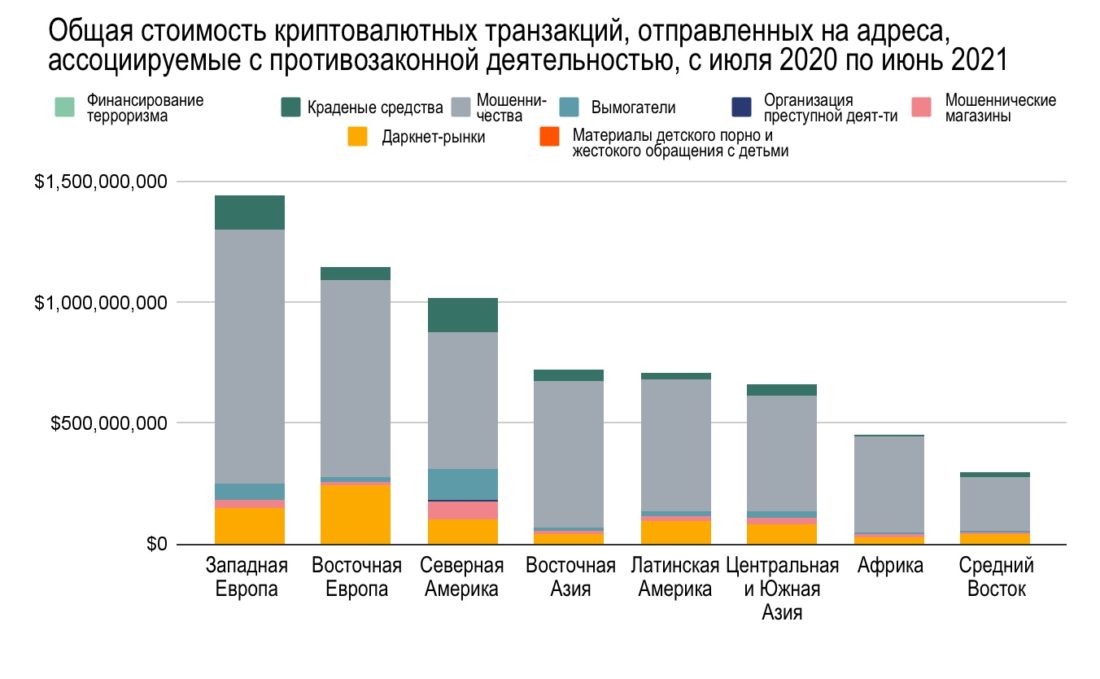
It is also noteworthy that Eastern Europe is larger,than any other region in the world sends cryptocurrencies to darknet markets. This is largely due to the Hydra trading platform. Hydra is the world's largest darknet marketplace and serves almost exclusively users from Russian-speaking countries in Eastern Europe. However, as in all regions, the largest share of funds sent from Eastern Europe to addresses associated with illegal activity is to addresses associated with fraudulent schemes. It can be assumed that most of this money is a transfer of funds from victims to scammers. Between June 2020 and July 2021, Eastern European blockchain addresses sent a total of $815 million to scammers, second only to Western Europe.
Eastern Europe also accounted for the majority of web traffic to fraudulent sites by a significant margin over the same period.

Refining the picture down to the country level, we see that Ukraine is the largest source of this web traffic, more than twice the country in second place.

What kind of scammers threaten cryptocurrency users from Eastern Europe? More than half of the value sent from the region to scam projects came from one scam: Finiko.
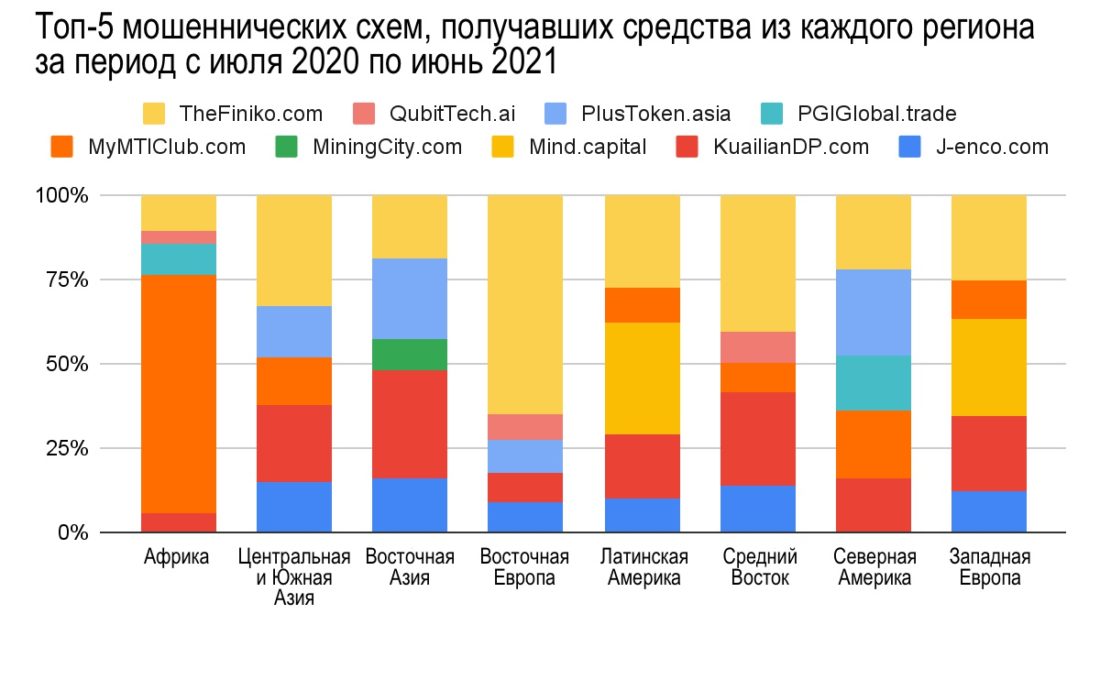
Finiko was a Russian financial pyramid,which collapsed in July 2021, shortly after users reported that they could no longer withdraw funds from their accounts with the company. Finiko offered users to invest in BTC or Tether, promising monthly returns of up to 30%, and eventually launched its own coin, which was traded on several exchanges.

AlongdataThe Moscow Times, Finiko headed by KirillDoronin, a popular Instagram influencer, has previously been associated with other Ponzi schemes. The article notes that Finiko has managed to take advantage of difficult economic conditions in Russia, exacerbated by the Covid pandemic, by attracting users desperate to earn extra money. Chainalysis' analytics tools show just how big this scam was.
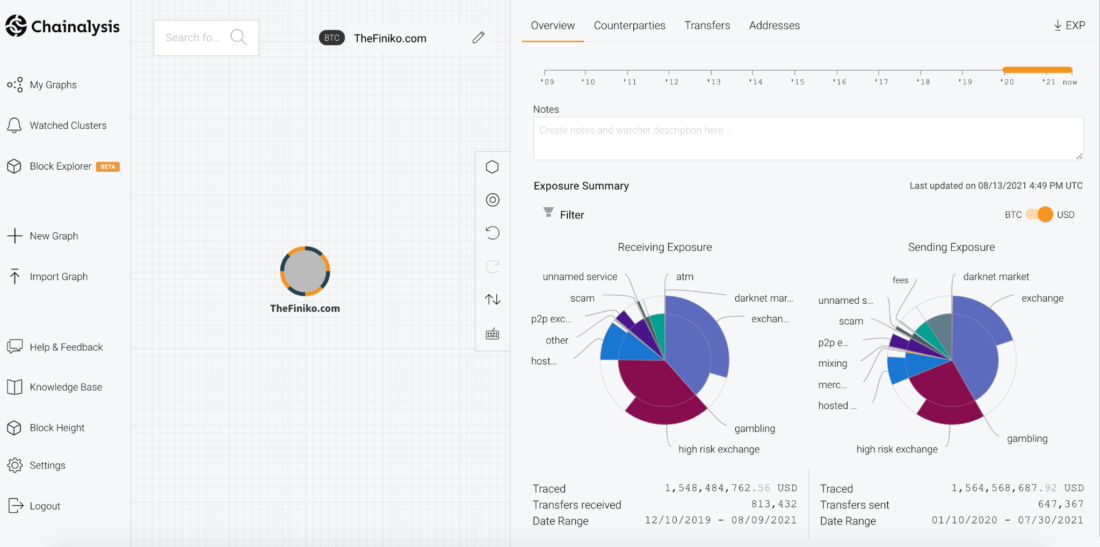
Between December 2019 and August 2021 Finikoreceived over $1.5 billion worth of Bitcoin in over 800K individual transfers. While it is unclear exactly how many individual victims made these deposits, nor how much of that $1.5 billion was paid out to investors to support the scheme, it is clear that Finiko is a massive scam targeting Eastern European cryptocurrency users, predominantly from Russia and Ukraine.
Eastern European addresses also receive a large amount of funds from fraudulent addresses, which suggests that in addition to victims, there are many fraudulent operators in the region.
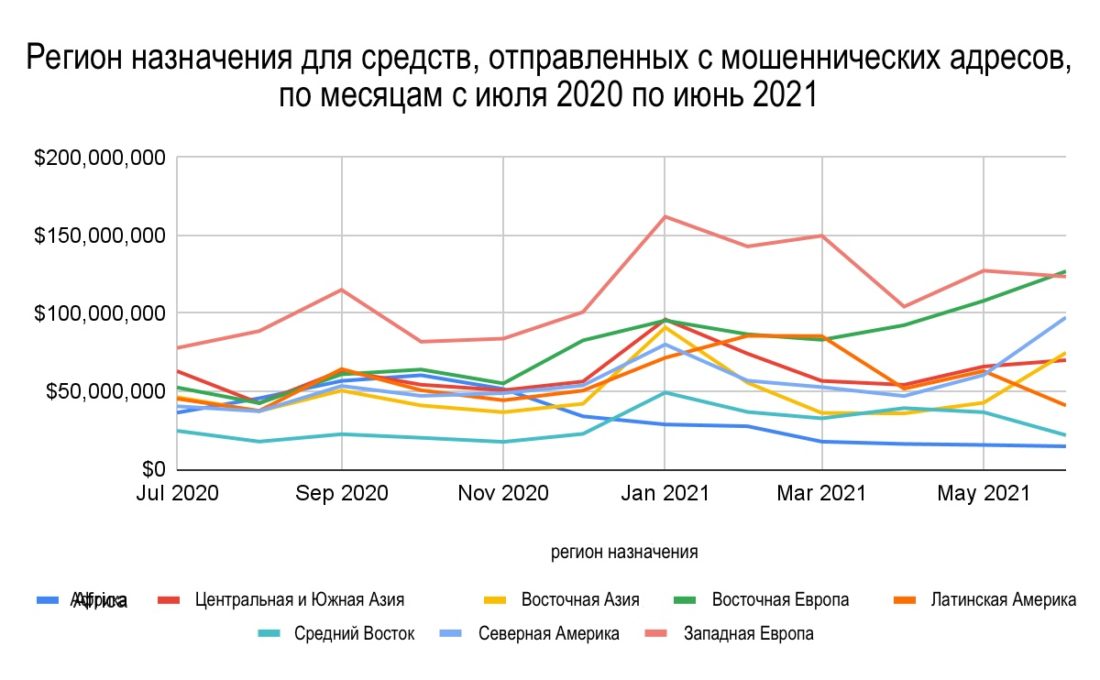
The diagram above shows the dynamics of receivingregions of funds from fraudulent schemes over the past year. During this period, Eastern European addresses received approximately $950 million worth of cryptocurrency from fraudulent addresses, again second only to Western Europe. However, Eastern Europe's monthly numbers have risen steadily since March 2021, while Western Europe's have declined, causing Eastern Europe to overtake Western Europe in the amount of cryptocurrency transactions originating from fraudulent addresses in June. Again, more than half of these funds come from Finiko.
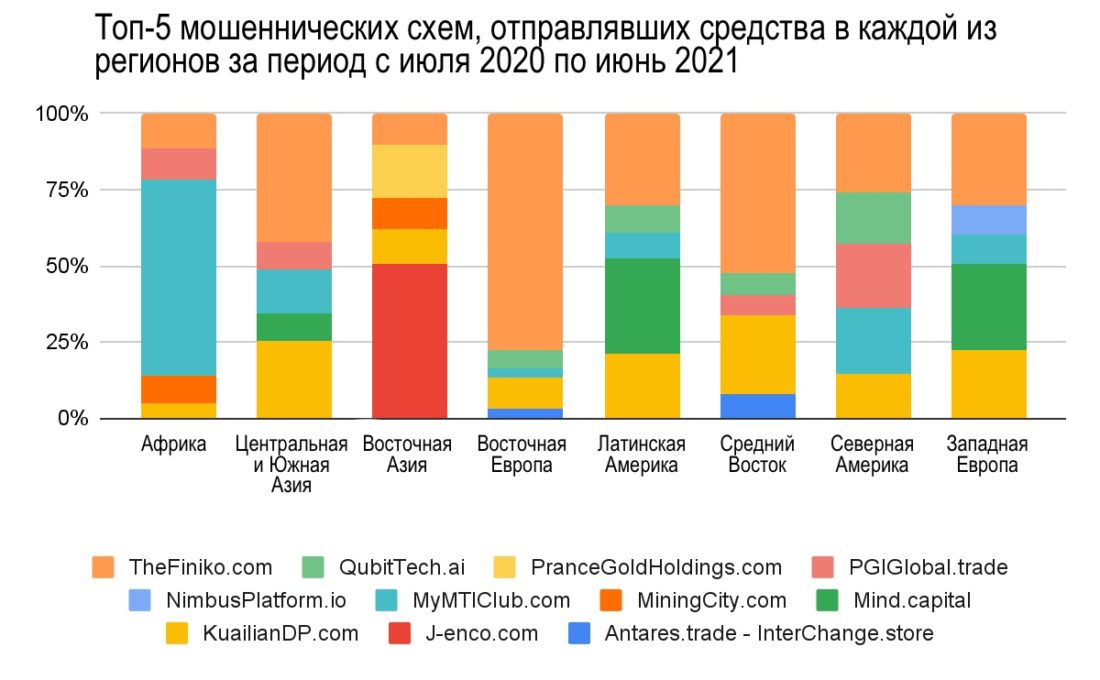
Eastern European addresses also receivedsignificant amounts of funds from addresses associated with extortion: $46 million, second only to Western Europe ($51 million). However, we believe that at least some of the ransomware money sent to Western European addresses would most likely also be correctly attributed to Eastern Europe. The geographic attribution used in the study is based on web traffic to cryptocurrency services, so in cases where two regions use many of the same services, it is more difficult to properly differentiate between them.
The matrix below shows which regions havethe largest overlap in terms of services used. Each cell indicates the number of services for which the region indicated in the column is the main source of web traffic, and the region indicated in the row is the second for this indicator.
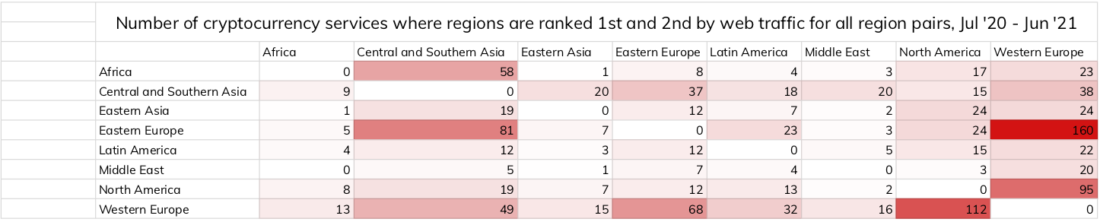
The number of cryptocurrency services for which these regions rank 1st and 2nd as sources of web traffic for all pairs of regions for the period from July 2020 to June 2021
It can be seen from the matrix that of all pairs of regionsEastern (BE) and Western Europe (WE) have the greatest traffic coincidence: 160 services with WE as the main and BE as the second most important traffic source and 68 services with an inverse ratio between these two regions. Therefore, we believe that some of the cryptocurrencies marked as being moved from ransomware addresses to Western European addresses are probably actually going to Eastern Europe.
Why are the authors so confident about thisdistortion and not the opposite? A study published by Chainalysis in May suggests that many of the most common ransomware strains are associated with cybercriminal groups based in or associated with Russia, such as the acclaimed Evil Corp, whose leadership, according to the US government, is associated with the Russian government. However, there is another way to get an idea of what part of the ransomware activity cybercriminals from Eastern Europe are responsible for, besides tracking where the ransomware operators are sending funds to cash out. Many ransomware viruses affiliated with Russia and other Eastern European countries have code that prevents them from being used against operating systems in the CIS countries. The chart below shows how much of the total ransomware revenue in 2020 and 2021 came from strains associated with Evil Corp or with a code that prevents the use of these viruses in the CIS countries.
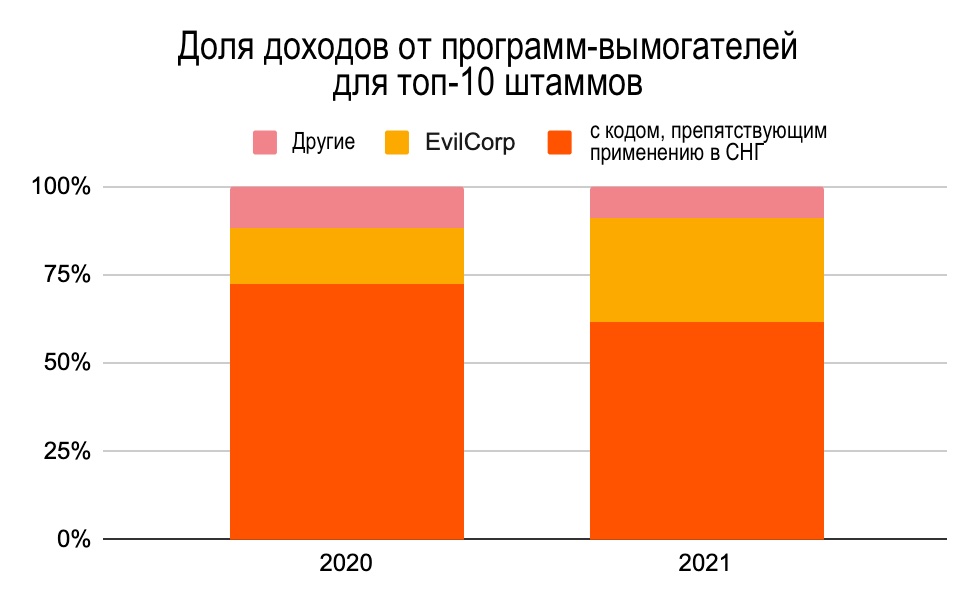
In general, during the study period, the strainsransomware associated with Eastern Europe and included in the top ten strains make up 90% of the total ransomware payments, and this share is growing from year to year.
</p>





