A "51% attack" or "double spend attack" on a blockchain involves a miner or group of minersare trying to spend twice theircryptocurrency in this blockchain. They are trying to make a "double waste" - this is where the name comes from. However, their task is not always the double waste of cryptocurrency. More often, this is arranged in order to discredit some cryptocurrency or blockchain, affecting their integrity.
Here is a small example: Suppose I decided to spend 10 bitcoins on a luxury car. A few days later, a car is delivered to me, and the bitcoins from my wallet are transferred to the car seller. Carrying out a 51% attack on the Bitcoin blockchain, I can try to reverse this Bitcoin transaction. If I succeed, I will become the proud owner of both a luxury car and my own bitcoins, thereby getting the opportunity to spend the same bitcoins again. The very concept of such an attack may seem obvious from the point of view of the democratic blockchain, but there is a widespread misconception about how it actually works. This short article will attempt to provide a clear and more detailed explanation of the 51% attack mechanism. If you still do not know how miners add transactions to the blockchain, I recommend that you first read this article; reading it will not take you much time. And if you are not familiar with how the blockchain works, then perhaps you should start here.
Blockchain = management
Before going into details of work51% attack mechanism, it is important for us to understand that blockchain protocols are essentially a form of control. The blockchain manages a data registry, for example, transaction data. And since the blockchain protocol itself can manage this in our place, we no longer need the services of third-party intermediaries, such as a government or a bank. This is what makes (most) blockchains decentralized. The Bitcoin blockchain protocol is based on the principles of democracy. This means that the decision on the truth of a particular version of the blockchain will be carried out by the majority of participants (miners) in its network.
How the attack occurs 51%
When the owner of the bitcoin confirms the transaction,it is placed in one of the local pools of unconfirmed transactions. Miners select transactions from such pools to form a block of transactions. In order for this block of transactions to be added to the blockchain, they need to solve some very complex mathematical problem. They are trying to find a solution using the computing power at their disposal. This process is calledhashing(more about the hashing algorithm you canread here). The more computing power a miner has, the higher his chances of finding the right solution faster than other miners find theirs. When a miner finds a solution, it will be broadcast (along with its block) to all other miners in the network, who will only validate the solution if all transactions within that block are valid, according to the existing transaction record on the blockchain.It should be noted that even an attacker minerhe will never be able to create a transaction on behalf of someone else, because for this he will need to know the digital signature of that person (his private key). Sending bitcoins from someone's account is therefore simply impossible unless the corresponding private key is available.
Secretive mining - creating a secret side chain in the blockchain
Now pay attention!A malicious miner, however, could attempt to revoke existing transactions. When a miner finds a solution to a block, it must be broadcast to all other miners for verification, after which the block is added to the blockchain (miners reach consensus). However, a rogue miner can create a side chain (hidden) of the blockchain by not transmitting the solutions of his blocks to the rest of the network. In the end it turns outtwo versionsone blockchain.
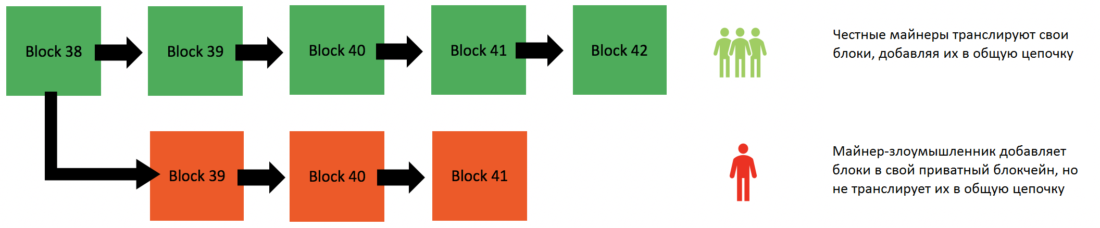
Now there are two versions of one blockchain. The red chain can be considered to be produced in stealth mode.
One version is that followed by the respectableminers, and the second uses a malicious miner. This fraud miner now works with its own version of the blockchain and does not broadcast it to the rest of the network. The rest of the network does not take this chain into account, for the simple reason that it was not broadcast. It is isolated from the rest of the network. An attacker can now spend all his bitcoins in the true version of the blockchain, the one that all other miners are working on. Suppose, for example, that he will spend them on the purchase of a Lamborghini. In the true version of the blockchain, its bitcoins will be considered spent. Meanwhile, he does not include these transactions in his isolated version of the blockchain. In his version, he still owns these bitcoins.
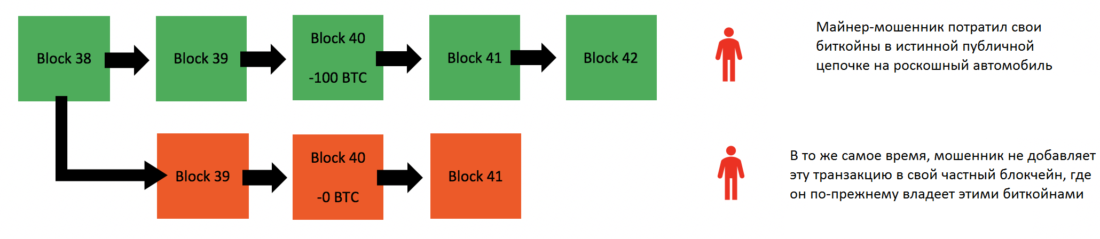
A fraud miner excludes its own transactions from its private blockchain.
Meanwhile he is still collecting blocks andverifies them all independently in its isolated version of the blockchain. This is where all the trouble starts … Blockchain is programmed to follow the model of democratic governance, in other words, governance by the majority. In the blockchain, this is implemented through the obligatory following of the longest (actually the heaviest, but let's not complicate things too much) chain, because the majority of miners add blocks to their version of the blockchain faster than the rest of the network (therefore, the longest chain = the majority). This is how the blockchain determines which version of the chain is true, and therefore what the balances of all wallets are based on. And here the race begins. Whoever has the most hashing power will add blocks to their version of the chain faster.
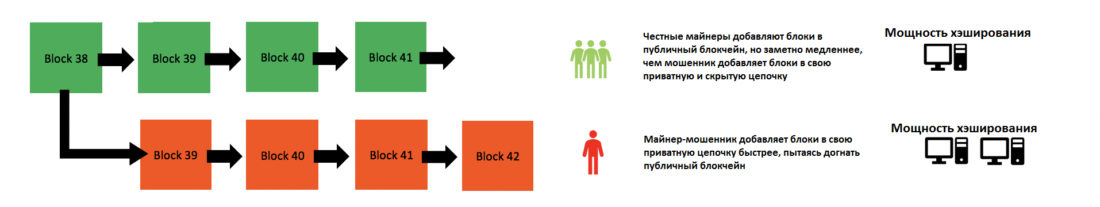
The fraudulent miner, with greater hash power, quickly adds blocks to its private chain.
Race - cancellation of existing transactions by broadcasting a new chain
Now the attacker miner will try to addblocks to their isolated blockchain are faster than other miners add blocks to their blockchain (the one that is true). And as soon as the fraud miner creates a longer blockchain, he suddenly broadcasts his version of the blockchain to the rest of the network. The rest of the network will see that this (substitution) version of the blockchain is actually longer than the one they worked with, and the blockchain protocol will force them to switch to this (substitution) chain.
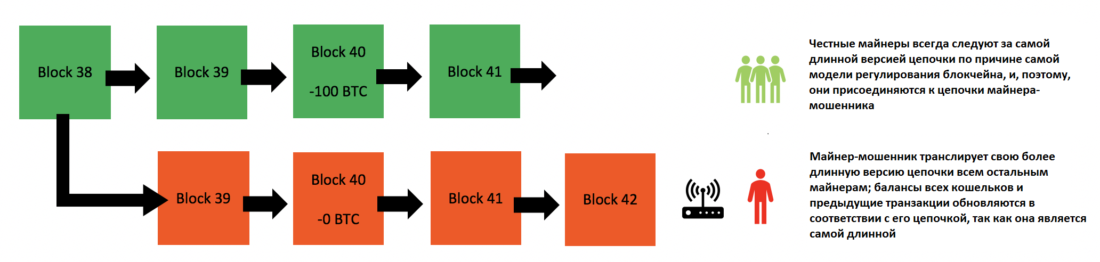
An attacker miner broadcasts its chain of the rest of the network as soon as it becomes longer (heavier) than the original chain.
The distorted blockchain is now considered trueblockchain, and all transactions that are not included in this chain will be immediately canceled. The attacker had previously spent his bitcoins on Lamborghini, but this transaction was not included in his hidden chain, the one that is currently the main one, and thus, those spent bitcoins are again at his disposal. And he has the opportunity to spend them again.
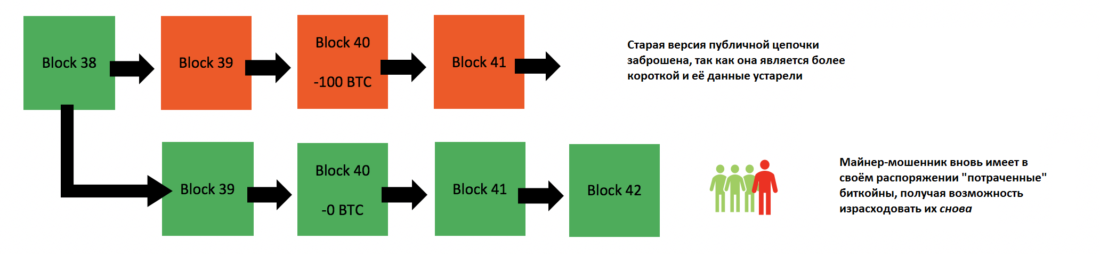
All other miners must reorganizetransaction history in its chains, taking as a basis a replacement chain, since it is heavier. And this story does not include the spending of those 100 bitcoins.
This is a double spend attack(double spending).It is commonly referred to as a 51% attack because the malicious miner who plans it will need hashing power greater than the combined hashing power of the rest of the network (hence the 51% hashing power figure) in order to add blocks to their version of the blockchain faster, which will ultimately allow him to build a longer chain.
So how is Bitcoin protected from this?
In practice, such attacks are extremely difficult to carry out. As mentioned earlier, the miner will require hashing power that exceeds that of the rest of the networkput togetherso that his attack is successful. And taking into account the fact that there may be hundreds of thousands of miners in the Bitcoin blockchain, such an attacker-miner will have to spend enormous money on mining equipment to compete with the rest of the network. Even the most powerful computers in the world cannot directly compete with the total processing power on this network. You can find countless arguments against the attack 51%. For example, the risks of being caught and prosecuted, in addition to the cost of electricity, renting premises for storing all this mining equipment, marking traces and money laundering. An operation of this kind, in simple terms, will require too much effort compared to what it would give an attacker in return, at least in the case of the Bitcoin blockchain.

Are other blockchains vulnerable?
Another interesting news iswhich, no matter how difficult it will be to carry out such an attack, 51% of the attacks actually took place in the past. In fact, one of these attacks was made relatively recently (in April 2018) on the Verge blockchain (XVG). In this particular case, the attacker discovered an error in the code of the Verge blockchain protocol, which enabled him to produce new blocks at an extremely fast pace, thereby allowing him to create a longer version of the Verge blockchain in a short time. This example illustrates an event that may contribute to a 51% attack, but which is very rare and mainly due to an error in the protocol code. An authoritative team of blockchain developers will probably notice a similar bug and prevent its malicious use.
When studying the algorithm of "confirmation of completionwork ”/“ Proof of Work ”we learn that the presence of large hashing power leads to greater security against 51% attack. Smaller altcoin blockchains based on this algorithm can be much more vulnerable to such attacks, given that attackers do not need significant computing power to carry out the attack, due to the small total hashing power in such blockchains. For this reason, 51% attacks are usually conducted, if at all, against small blockchains (e.g. Bitcoin Gold). Bitcoin blockchain, by the way, has never before been the victim of a 51% attack.
ASIC mining - advanced mining equipment
It also brings us to one of the last“Hot” topics in blockchain mining using ASIC devices. ASIC mining technology was developed by various early Bitcoin mining companies to improve mining equipment, making it much more powerful. There is much debate about whether ASIC-based hardware makes some individuals or mining groups too powerful due to increased capacity. The Monero blockchain (XMR) recently updated its blockchain protocol, which blocked the use of ASIC mining in this blockchain. As a result of the upgrade, the total hash power in the Monero network fell by a staggering 80% (see below)!
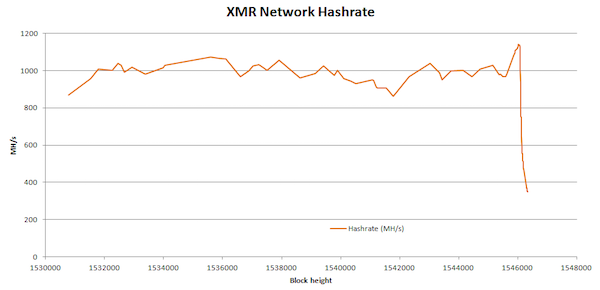
Computing power in the XMR network fell by 80% after blocking ASIC mining!
This event is an indicator of how muchMonero blockchain capacities were in the hands of miners using ASIC equipment. Perhaps this would not be a problem if all the network participants used mining equipment based on ASIC technology. In fact, the problem is that giant mining companies, such as Bitmain, are suspected of controlling a large number of operations using ASIC mining. And even despite the fact that such organizations provide this technology to private individuals, it is assumed that this happens only after they themselves use it first for a long time. Some people on the blockchain argue about whether this fact makes such companies too powerful or not. Ideally, the blockchain should be managed by as many miners as possible. In the end, this is what makes the blockchain more decentralized.

How does one of the Bitmain mining farms in Inner Mongolia, China look from the inside.

Another huge mining complex.