Article Reading Time:
4 min.

Most owners of BTC and other cryptocurrencies will probably not be able to say how much they have in stock with an accuracy of up to a satoshi. This is why they may become a victim of scammers.
What is crypto dust
“Crypto dust” is a small amount of cryptocurrency that can be sent en masse to different wallets. The goals of the sender may be completely different.
In general, "dust" represents the amountcryptocurrencies equal to or less than transaction fees. Thus, the smallest unit of Bitcoin is one Satoshi - 0.00000001 BTC. Therefore, even 0.00000500 Bitcoin today is “dust”.
Often it ends up on stock exchanges.It cannot be traded. Thus, she is in limbo. It is often used for absolutely peaceful purposes - for example, sending “dust” to wallets is done for advertising purposes in order to attract more people to cryptocurrency or another project.
However, recently, so-called “dust attacks” have become widespread. But they do pose a certain threat.
What is a dust attack
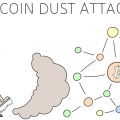
“Dust attack” is the sending of crypto dust toa large number of addresses from attackers. As a rule, this is expressed in the fact that scammers want to track the identity of the owner of the wallet. How does this happen?
Blockchain itself does not require anypersonal data. But the problem is that the transactions in it are visible to everyone. Thus, it is possible to track which specific transactions and in what volume were carried out from a particular address.
Dust attack is not a direct way to stealcryptocurrency. Having given you crypto dust, scammers are only trying to track who you are through a series of your transactions. Most users will not pay attention to parts per million.
In general, a dust attack can occur duringmany blockchains, not just Bitcoin. With its help, scammers try to gain access to personal data of individuals and legal entities. After this, they begin to use various methods to extract their benefits: threats, extortion, blackmail, and so on.
When is crypto dust useful?
Dust attacks are just one way to use crypto dust. For the most part, it is absolutely harmless, and can even be beneficial.
For example, developers can send dust,to check the functionality of your hardware or updates. It can also be distributed among wallets if they need to run a test to eliminate the threat of a hacker attack or other vulnerability.
Traders can make profits in the form of dust.After all, each transaction is determined by the price at which you bought and at what you sold. Sometimes crypto exchanges offer to exchange crypto dust for their tokens or some other cryptocurrency.
Governments can also use dust attacks to track potential criminals, terrorists and others.
Working principle of dust attack
The first thing scammers count on ispeople's inattention to detail. Few people will notice that some shares of cryptocurrency suddenly appeared on the account. The next thing the scammers are counting on is that the recipient of the crypto dust will start making transactions with it as if nothing had happened. If this does not happen, then the whole idea turns out to be unprofitable.
When a dust attack victim sendscryptocurrency to a centralized platform, he will not notice that he will also send crypto dust along with it. This is an important point, since CEX is the one that requests a lot of personal data from clients. These are exactly what scammers are trying to get at by sending out crypto dust.
The most vulnerable to dust attacks arecryptocurrencies that use the unspent transaction balance (UTXO) model. This is because they create a new address for each change from a transaction.
What should you do to avoid becoming a victim of a dust attack?
Ways to protect against dust attack
The most important thing you must remember:the likelihood that you will fall for a scammer is not so high. Cryptocurrency holders, however, usually do not have a large amount of it. And for the sent dust, the attackers will still have to pay transaction fees, which have only grown in recent years in Bitcoin.
If transactions are not carried out, then tracknothing is possible. If you are still actively making translations, then you should take precautions. In general, there are a whole lot of them. But most of them require special education. However, there are also quite simple ones:
use tools that increase your anonymity online (of course, if it is legal in your country);
use hierarchically deterministic wallets that will themselves create new addresses for each subsequent transaction, which will create additional difficulties for fraudsters;
use programs that immediately convert crypto dust into native tokens.
If you follow these simple steps, the likelihood of you becoming a victim of a dust attack will be greatly reduced.