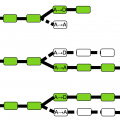
We have already figured out what a 51% attack is and that it is almost impossible to attack Bitcoin. But let'sWe will find out if this happened with younger cryptocurrencies.
We previously wrote material on vulnerabilityBitcoin to a 51% attack. We figured out that young cryptocurrencies that use the PoW (Proof-of-Work) consensus algorithm are most susceptible to the 51% attack – proof of work completion.
Cryptocurrencies that are just entering the marketusually a fairly small network hash rate. That is why it is quite easy for attackers to concentrate a “controlling stake” in their hands. Many new cryptocurrencies are forks or are simply based on existing ones and use the same mining algorithms. Thus, if any pool is already mining some popular cryptocurrency and contributes only a small share to the network hashrate, then by switching its powers to mining the newly appeared cryptocurrency with the same algorithm, the pool can easily capture 51% of the network hashrate. With monsters of the cryptocurrency world, such as Bitcoin and Ethereum, the likelihood of such an attack is practically reduced to zero due to its incredibly high cost and limited technical resources.
What threats does this attack pose and what benefits do attackers get?
Most often, the goal of attackers is doublespending the same coins (double-spending) – a transaction for a certain amount is sent to the exchange, and after receiving all the necessary confirmations and processing it by the exchange, the transaction is canceled and the funds are sent again, but to another exchange. Thus, the main victims will be the exchanges that paid the attackers funds for canceled transactions, but this will not cause direct losses to the coin holder. However, such a precedent will certainly cause reputational damage to the cryptocurrency as a whole.
It can also undermine the reputation of cryptocurrencyblocking transactions of ordinary users. Since the price of cryptocoins is, in most cases, determined by the market, the damage to reputation caused by the attack will significantly reduce their price, which will ultimately affect end users. In the case of a young cryptocurrency, such an incident could even lead to its complete market collapse. But even if the price falls, attackers can make a lot of money, because now many exchanges provide the opportunity for margin trading, which allows you to make a profit by playing on a falling price (by opening a position, a trader borrows the required amount of cryptocurrency and sells it on the market at the current price, and after the price decreases, the trader buys back the same volume, but at a lower price and returns what he borrowed, leaving himself the difference between the cost of sale and purchase). Due to the fact that an attacker can say with almost 100% probability that the rate of the attacked currency will go down – he can make very profitable trades on his exchange account without the risk of being associated with an attack.
What cryptocurrencies were attacked by 51%?
April 4, 2018 due to a bug in the mechanismblock signing, hackers were able to successfully carry out a 51% attack on the Verge network, while signing blocks not once every 30 seconds, as prescribed by the protocol, but once per second, forging the timestamp of the previous block. The problem was discovered by Bitcointalk forum user ocminer, while Verge officials initially tried to hush up the incident, calling it minor, but then acknowledged the problem and fixed the bug in the code within a few days. According to the official Verge version, the attackers managed to mine about 250 thousand coins, although according to calculations by Bitcointalk users, the figure was quite significant – almost 4 million coins. This attack caused the XVG price to drop by 25% within a few days. Unfortunately, Verge’s problems did not end there: on May 22, the SuprNova mining pool reported that the Verge network was again subject to a 51% attack, as a result of which all valid blocks were rejected over the course of several hours, which once again undermined the reputation of the cryptocurrency.
In May 2018, Bitcoin Gold's Communications DirectorEdward Iskra reported that from May 16 to 18, a 51% attack was carried out on the Bitcoin Gold network, as a result of which the attackers managed to steal up to 388,200 BTG (about $18.6 million at the exchange rate at the time of the attack) from exchanges and exchangers. The attackers obtained at least 51% of the network’s power (most likely, they used their own mining pool for this, as well as power rented from NiceHash). After gaining control of the network, they sent amounts from 8,000 BTG to 12,000 BTG to exchange addresses, creating a public blockchain and in parallel created a private blockchain by sending the same funds to their address GTNjvCGssb2rbLnDV1xxsHmunQdvXnY2Ft, waited for the required number of confirmations, changed the funds to another cryptocurrency and immediately they withdrew it, after which they canceled the entire public chain of blocks with a longer prepared private chain. The Bitcoin Gold developers recommended waiting for at least 50 confirmations from the network before the incoming transaction is fully processed. the longest canceled chain in this attack was 22 blocks (it was canceled by a chain of 25 blocks).
Another cryptocurrency affected inThe result of a code error in mid-May became MonaCoin. This attack cannot be called a full 51% attack, but it allowed one miner to replace the entire transaction chain from May 13 to 15. One of the miners managed to create two blocks in a very short time, instead of one, and start a private branch of the block chain, which was one block larger than the main one. Thus, after the publication of this branch on May 15, it was recognized by miners as the only true one since contained more blocks, and transactions of the main blockchain were canceled. As a result of the incident, the attackers managed at least 90 thousand dollars due to double spending.
June 2, 2018 on the official ZenCash channel51% reported a successful attack. Details were later published on the official blog. The purpose of the attack was to double spend funds. The thieves managed to steal at least 23152.3 ZEN (about 680 thousand dollars at the exchange rate at the time of the attack). The address used by the suspects – znkMXdwwxvPp9jNoSjukAbBHjCShQ8ZaLib, longest rejected chain – 38 blocks. Representatives of ZenCash immediately published a recommendation on how exchanges can secure their funds, in particular, they proposed increasing the number of confirmations to 100 and initiated a vote on increasing the complexity of the mining algorithm.
To draw attention to the problem of 51% attacks andThe website crypto51.app was created to demonstrate an estimate of the costs of implementing such an attack. Knowing the current network hashrate and the cost of renting miners, it is easy to calculate the cost of capturing 51% of the network power per unit of time. The data is obtained from several sources: the hashrate of networks is taken from the site “Mine The Coin”, the price of cryptocurrency from CoinMarketCap, prices for renting mining capacity from NiceHash. For example, one hour of attack on ZenCash currently costs about $5 thousand per hour. The cost of the attack calculated by crypto51 is only an estimate, but gives an idea of the reality of the attack. Although the costs of a 51% attack are quite high, up to 80% of the costs are offset by commissions and mining rewards.
As you can see, 51% attacks on youngcryptocurrencies are not only theoretically real, but have been repeatedly successfully implemented in practice. Most likely, the attacks will not stop there, and many newcomers to the cryptocurrency market will undergo similar tests for strength and readiness for adulthood among large market players.
Subscribe to ForkNews on Telegram.